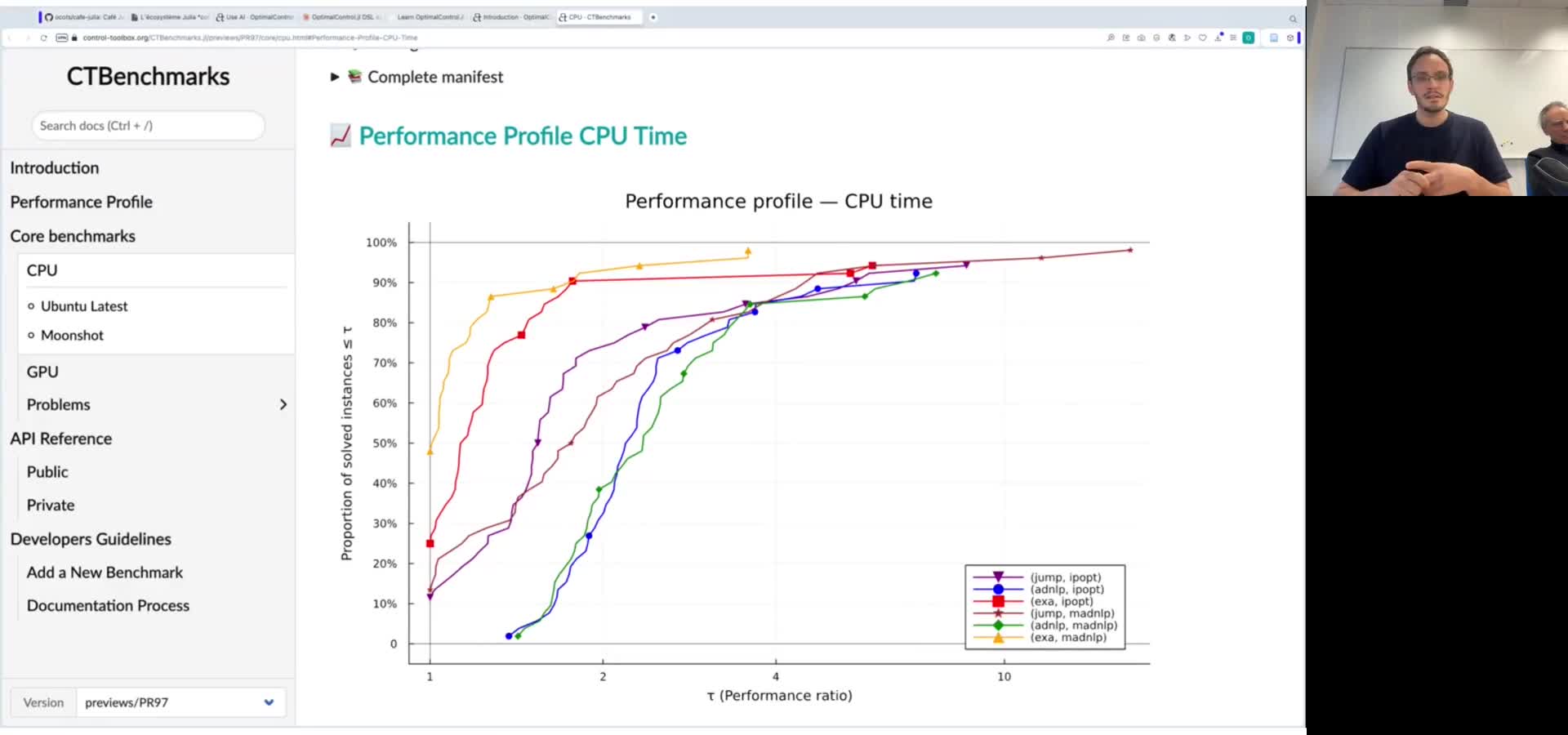
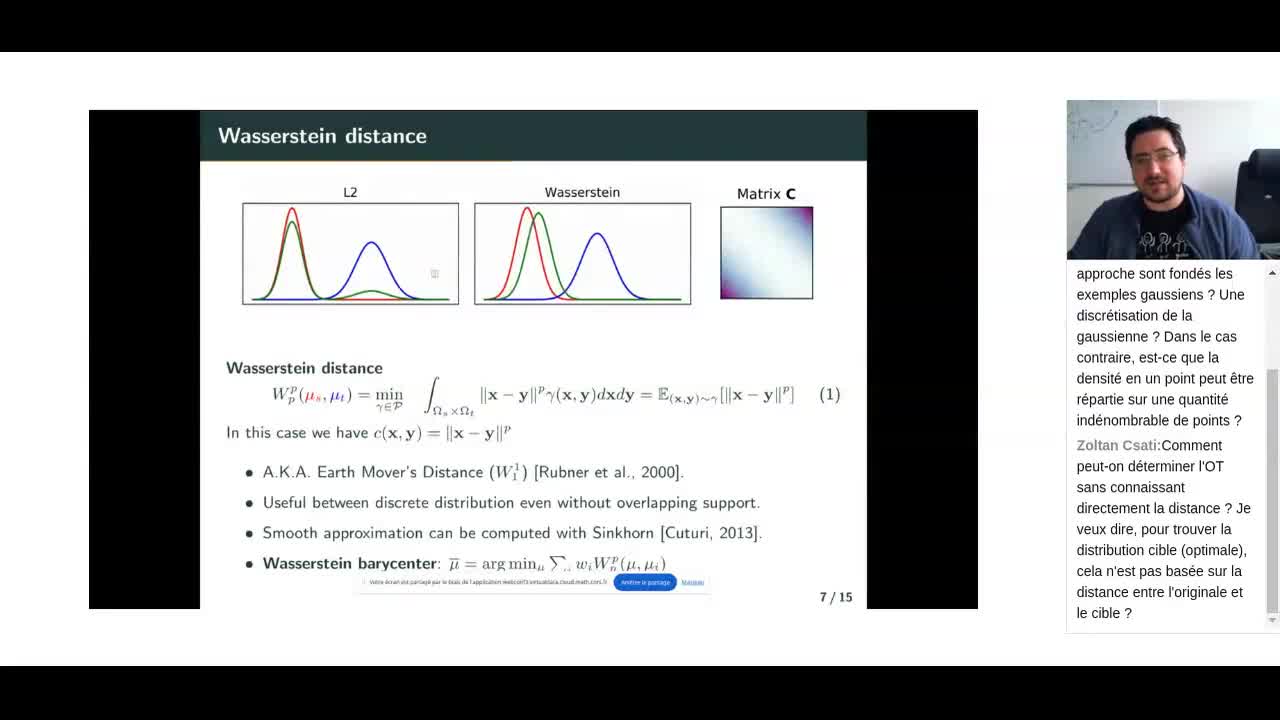
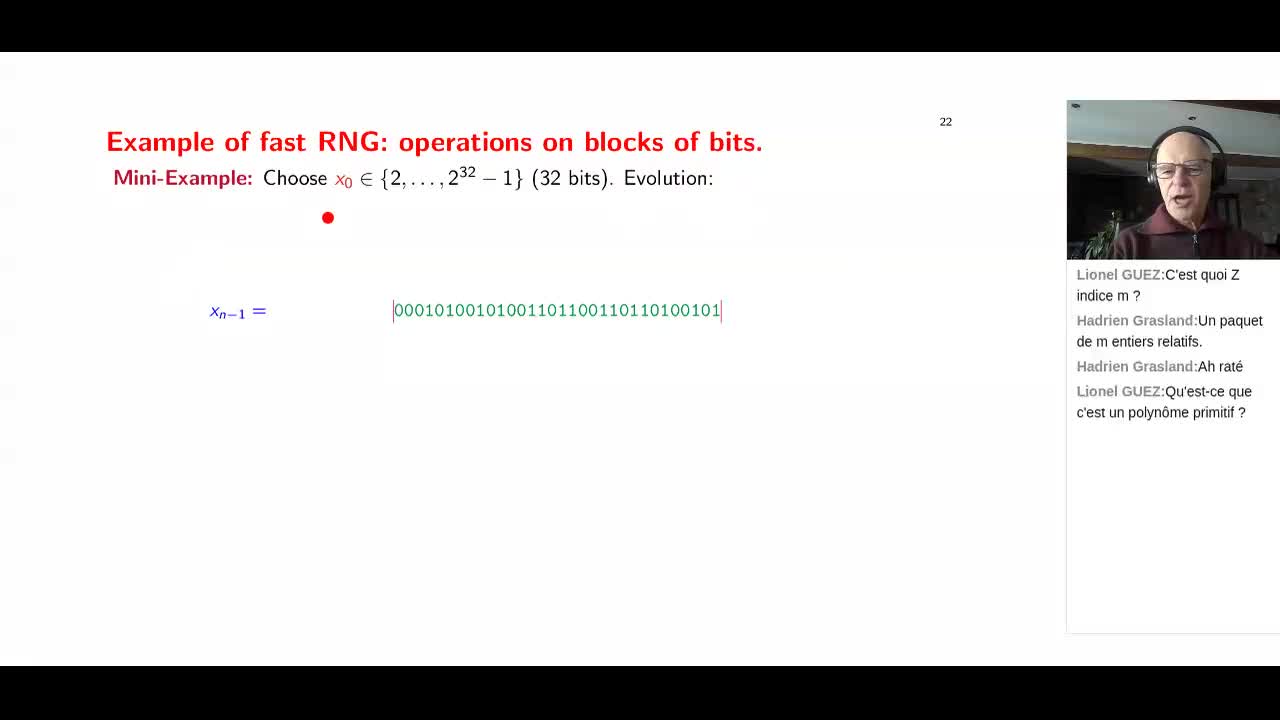
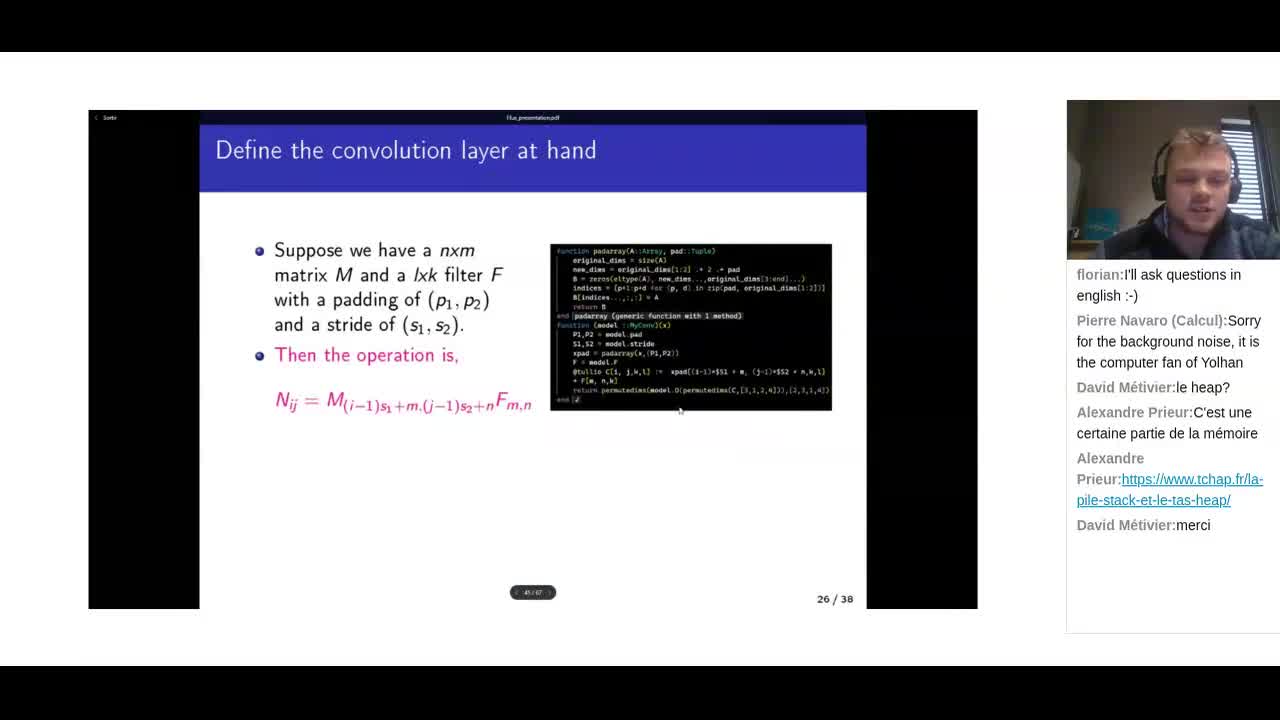
Café Julia: l’écosystème control-toolbox pour le contrôle optimal
Le projet control-toolbox rassemble plusieurs packages Julia pour modéliser et résoudre des problèmes de contrôle optimal. Autour du package central OptimalControl.jl, il propose une architecture