3: Message Attacks (ISD)

Descriptif
Table of contents
3.1. From Generic Decoding to Syndrome Decoding
3.2. Combinatorial Solutions: Exhaustive Search and Birthday Decoding
3.3. Information Set Decoding: the Power of Linear Algebra
3.4. Complexity Analysis
3.5. Lee and Brickell Algorithm
3.6. Stern/Dumer Algorithm
3.7. May, Meurer, and Thomae Algorithm
3.8. Becker, Joux, May, and Meurer Algorithm
3.9. Generalized Birthday Algorithm for Decoding
3.10. Decoding One Out of Many
Vidéos
3.1. From Generic Decoding to Syndrome Decoding
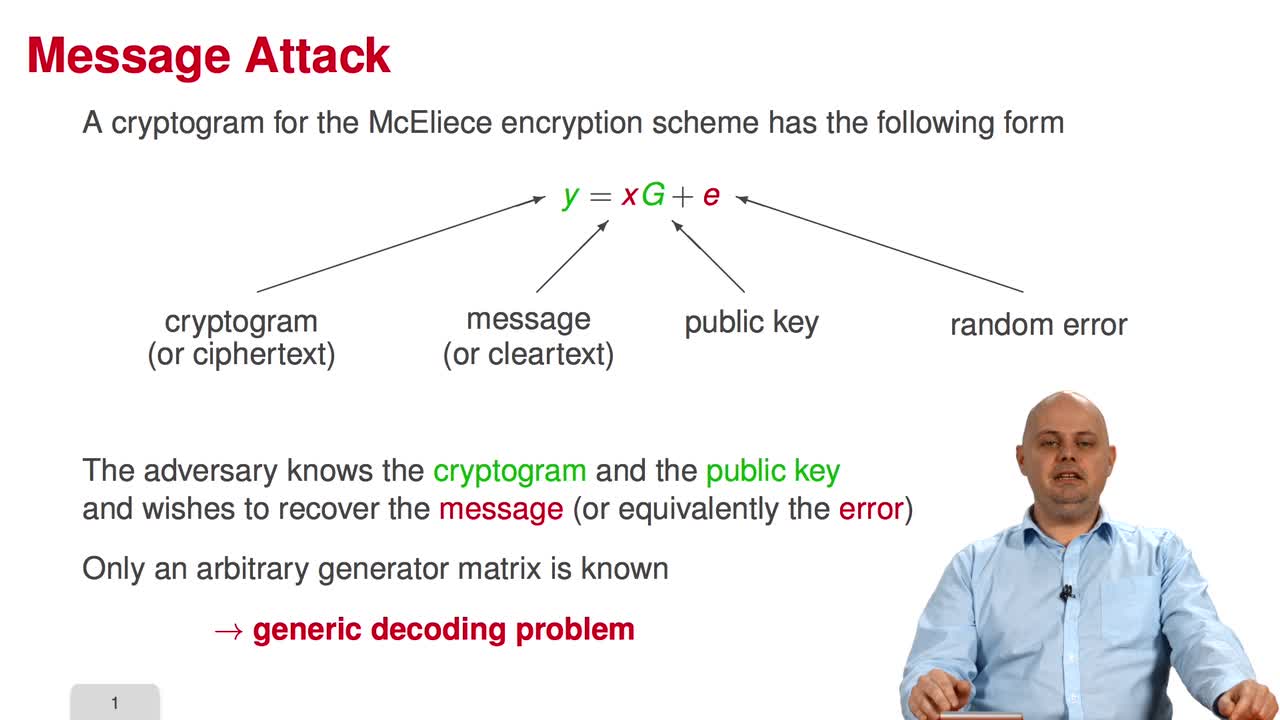
Welcome to the third week of the MOOC on code-based cryptography. This week, we will learn about message attacks. Among the ten sessions of this week, the first six will present the most essential
3.2. Combinatorial Solutions: Exhaustive Search and Birthday Decoding
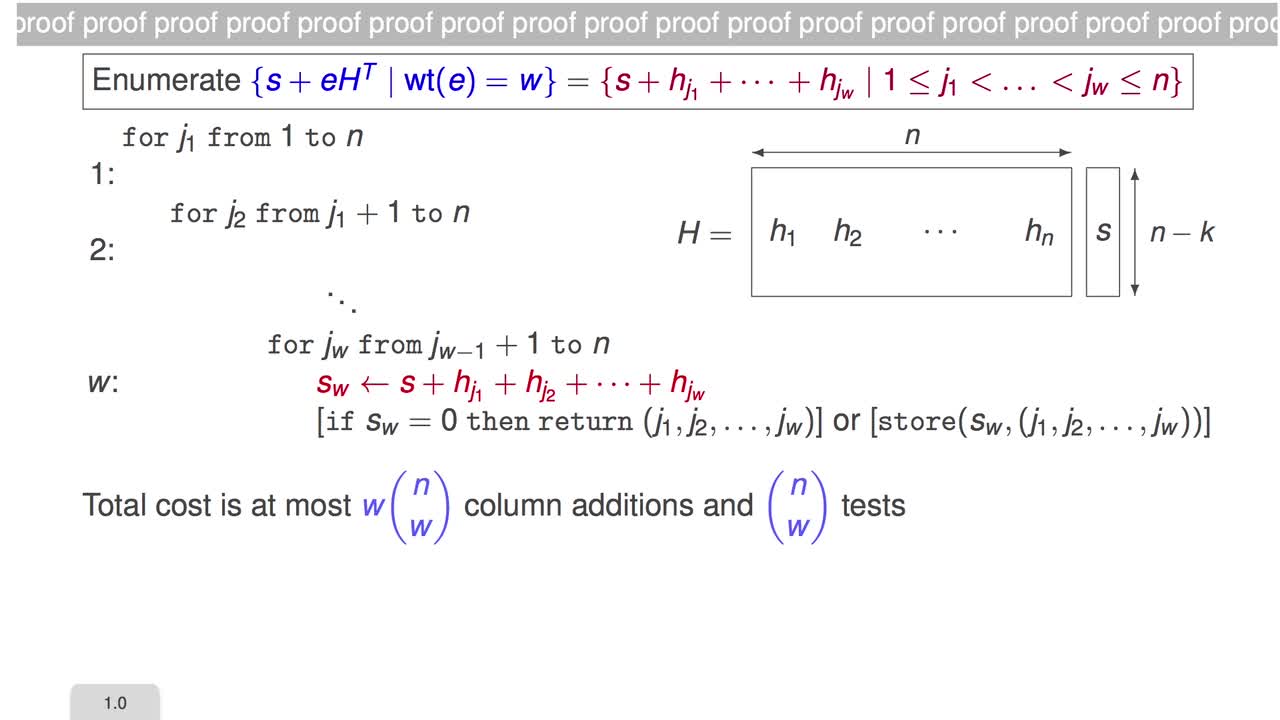
In this session, I will detail two combinatorial solutions to the decoding problem. The first one is the Exhaustive Search. To find our w columns, we will simply enumerate all the tuples j1 to jw
3.3. Information Set Decoding: the Power of Linear Algebra
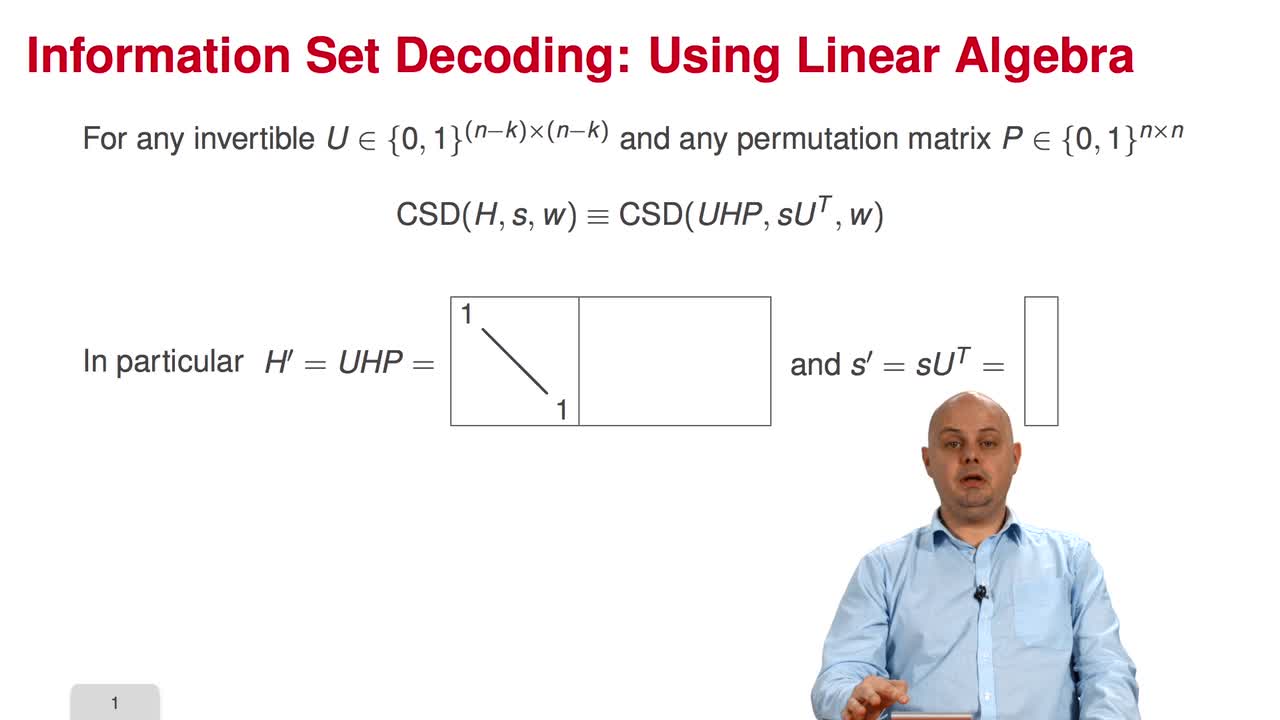
In this third session, we will present the most important concept of the week: Information Set Decoding. The problem of decoding is not only a combinatorial problem. Because we are dealing with
3.4. Complexity Analysis
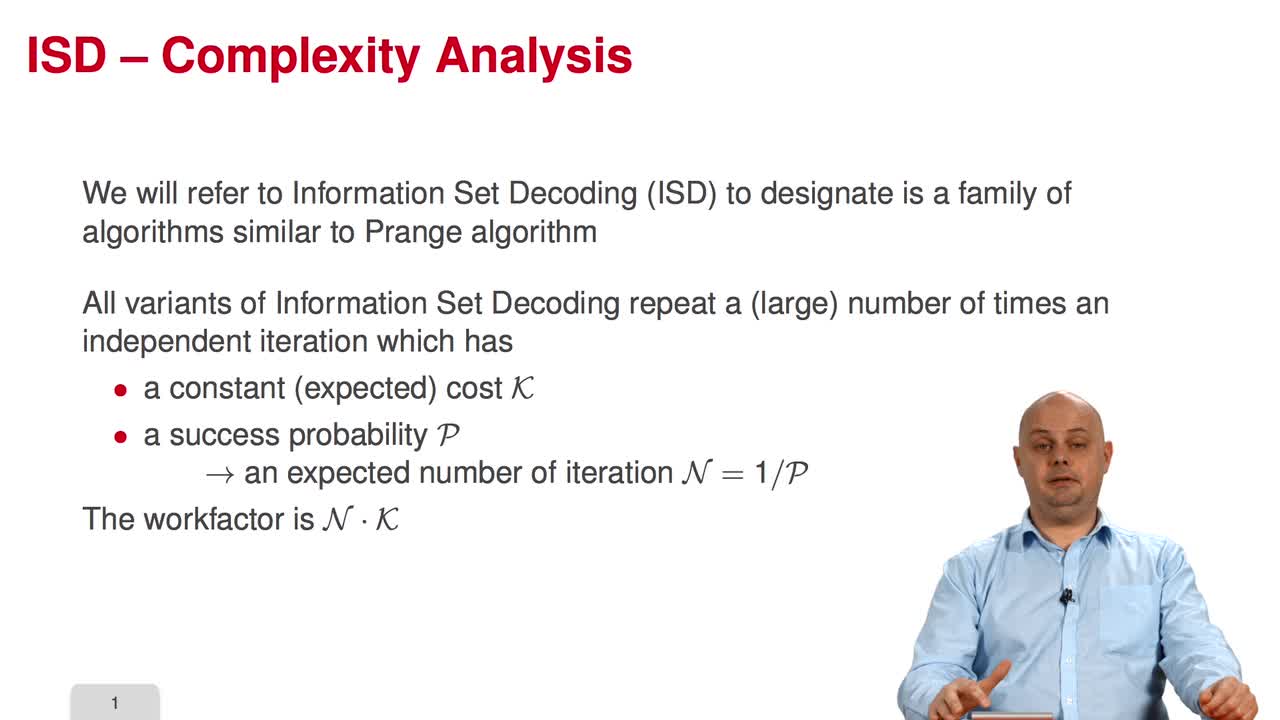
In this session, I will present the main technique to make the analysis of the various algorithms presented in this course. So, Information Set Decoding refers to a family of algorithms which is
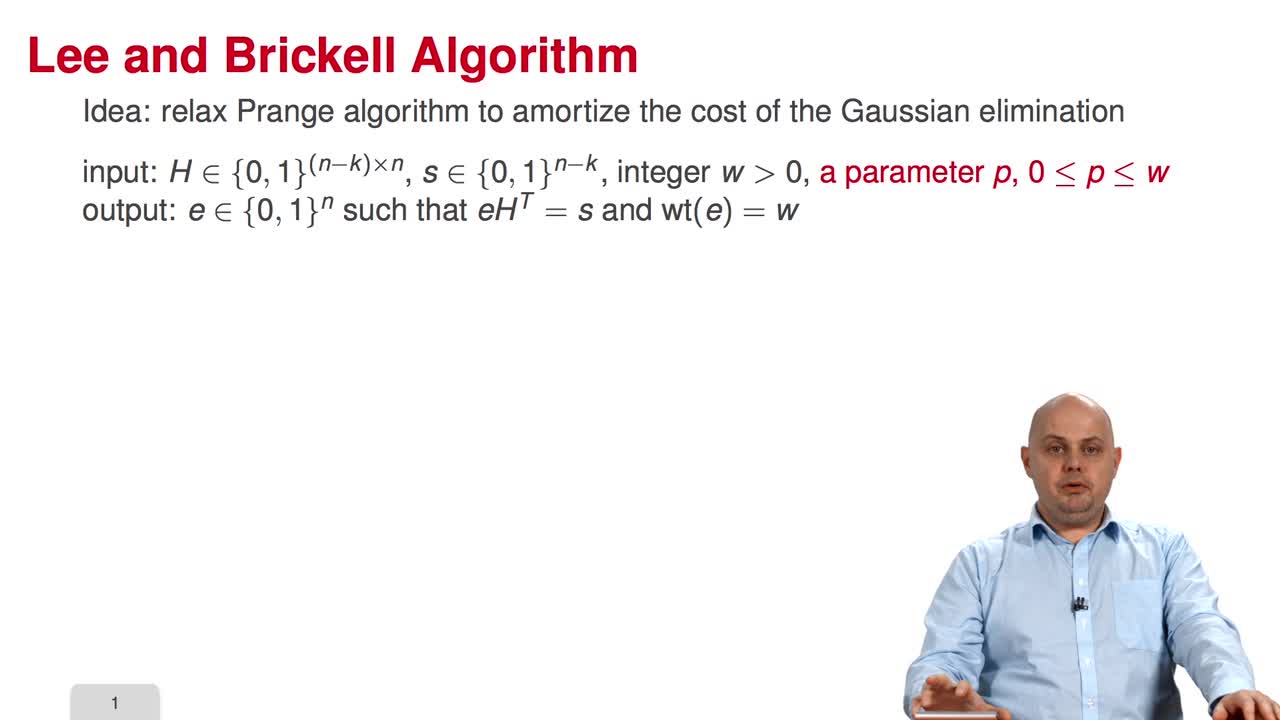
3.5. Lee and Brickell Algorithm
In this fifth session, we will study a variant of information set decoding proposed by Lee and Brickell. So, the main idea consists in relaxing the Prange algorithm to amortize the cost of the
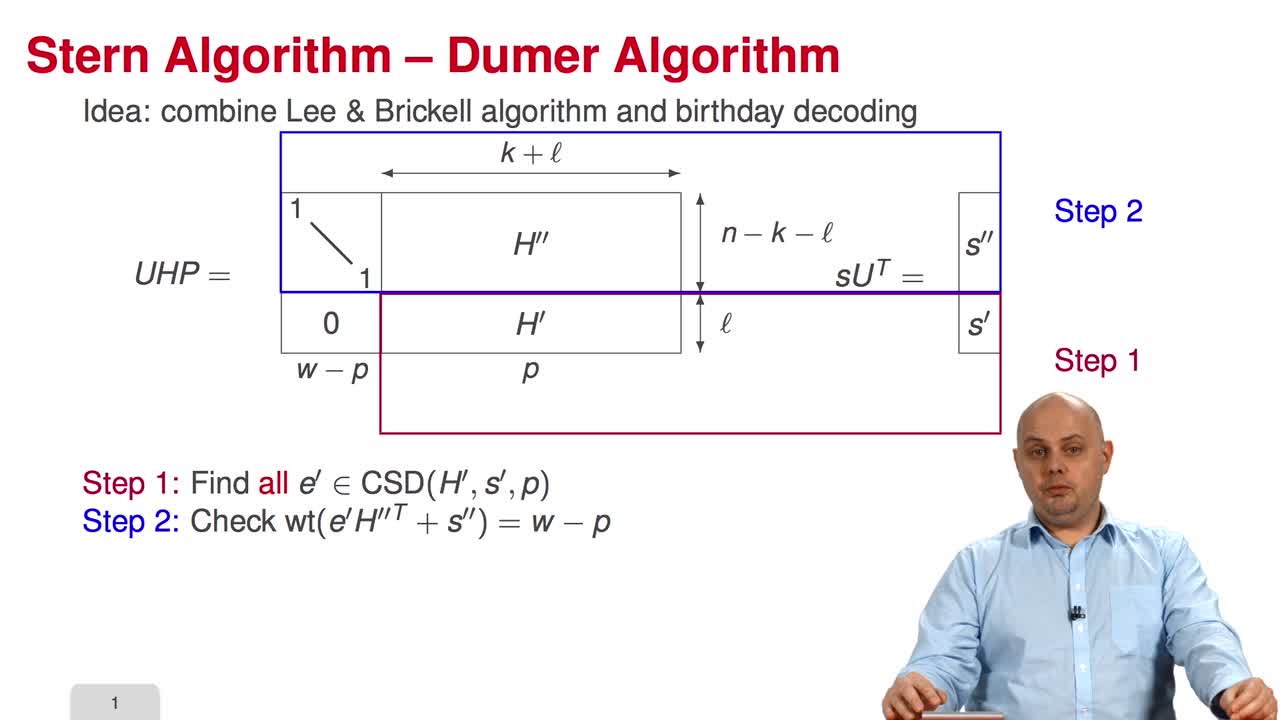
3.6. Stern/Dumer Algorithm
In this session, we will present the Stern algorithm for decoding. In fact, the idea is to combine two algorithms that we have seen before, the Lee and Brickell algorithm and the Birthday Decoding.
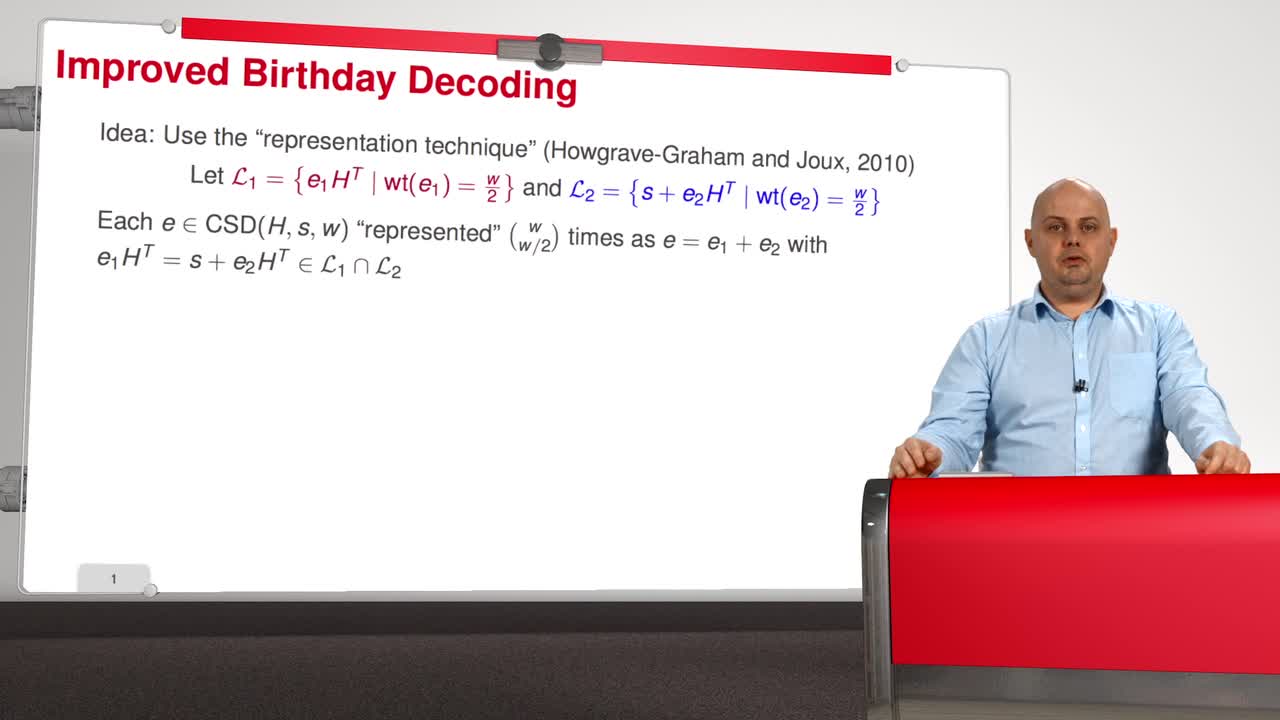
3.7. May, Meurer, and Thomae Algorithm
So, with the session 7 we are entering the most advanced part of that course. The idea of what I called the Improved Birthday Decoding is to use the so-called "representation technique" introduced
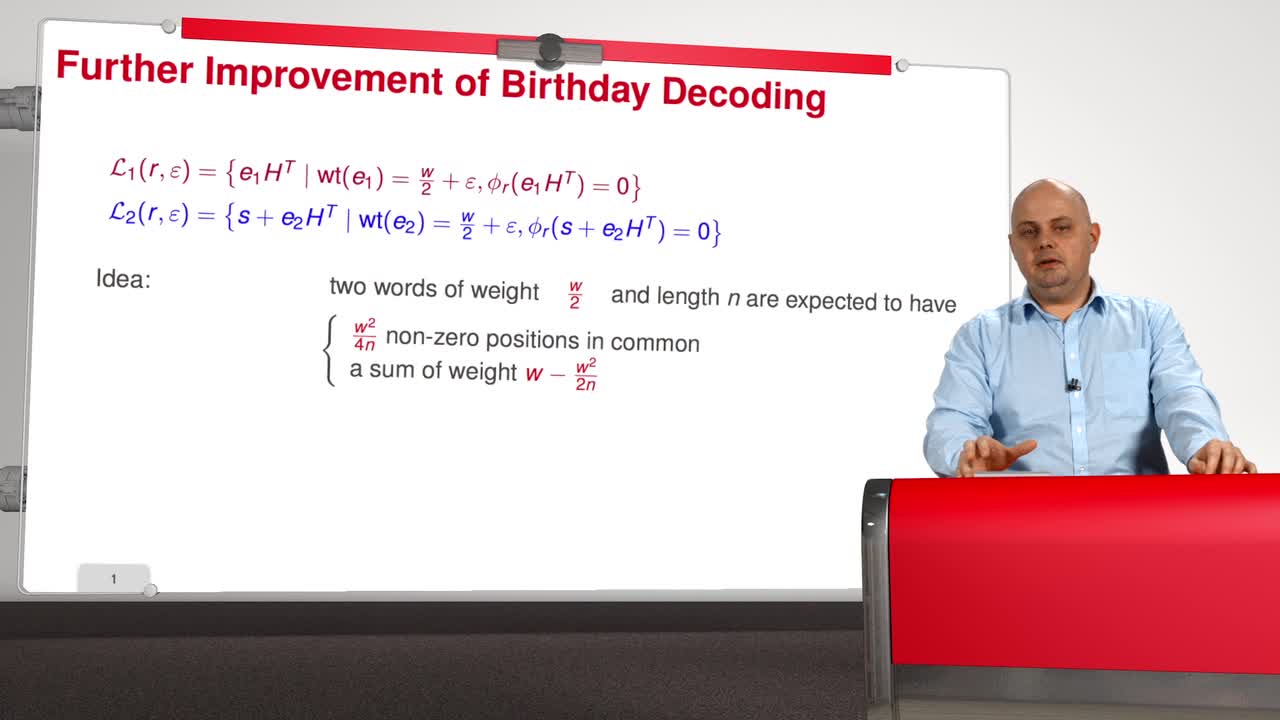
3.8. Becker, Joux, May, and Meurer Algorithm
Now in session 8, we will present yet another evolution of information set decoding. Before presenting this improvement, we will first improve the Birthday Decoding algorithm what I call a Further
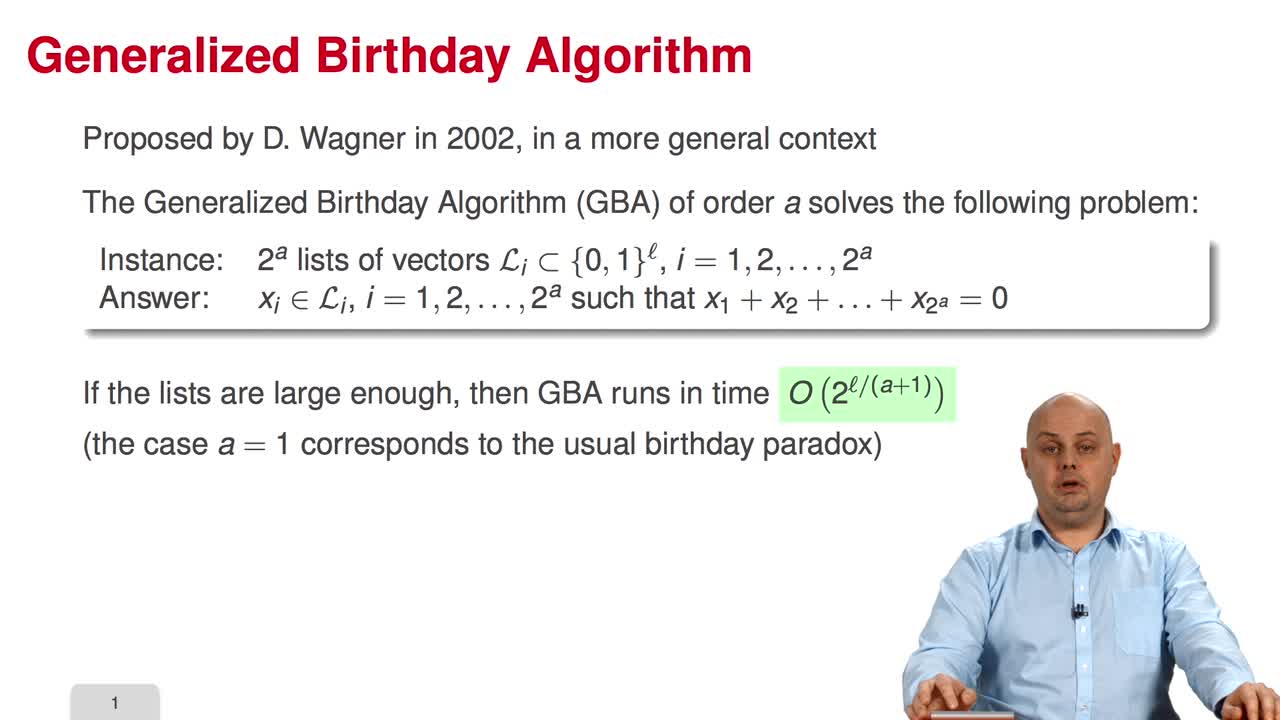
3.9. Generalized Birthday Algorithm for Decoding
The session nine is devoted to the application of the Generalized Birthday Algorithm to decoding. The Generalized Birthday Algorithm was presented by David Wagner in 2002, in a more general
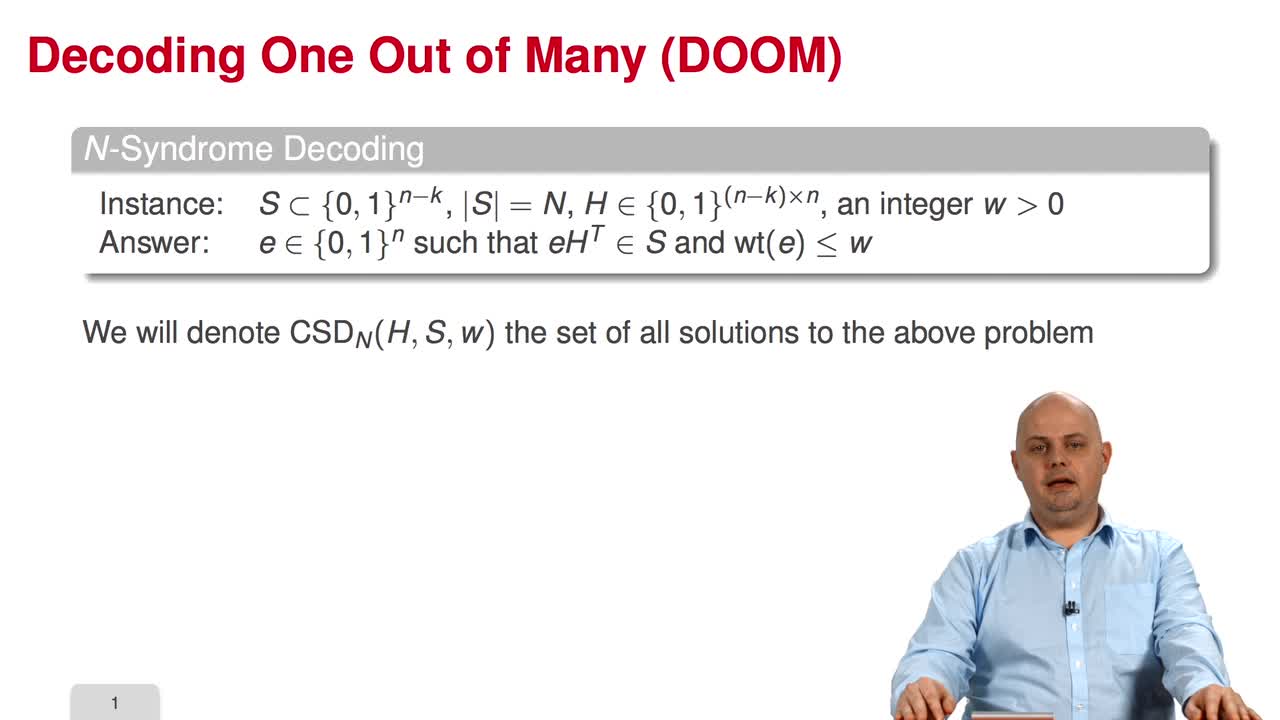
3.10. Decoding One Out of Many
The final session of this week is devoted to Decoding One Out of Many. Decoding One Out of Many is interested in solving the following variant of Syndrome Decoding. In this variant, the only
Intervenants et intervenantes
Auteur d'une thèse en mathématiques et informatique à l'Ecole polytechnique de Paris
Chercheuse à la faculté des sciences de l'université de La Laguna. Spécialités : code, cryptograhie et algèbre informatique (2015)
Enseignant chercheur en informatique à l'INRIA. Thèmes de recherche : Codes correcteurs d'erreurs et Cryptographie.