5: Other cryptographic constructions relying on coding theory

Descriptif
Table of contents
5.1. The Courtois-Finiasz-Sendrier (CFS) Construction
5.2. Attacks against the CFS Scheme
5.3. Parallel-CFS
5.4. Stern’s Zero-Knowledge Identification Scheme
5.5. An Efficient Provably Secure One-Way Function
5.6. The Fast Syndrome-Based (FSB) Hash Function
Vidéos
5.1. Code-Based Digital Signatures
Welcome to the last week of this MOOC on code-based cryptography. This week, we will be discussing other cryptographic constructions relying on coding theory. We have seen how to do public key
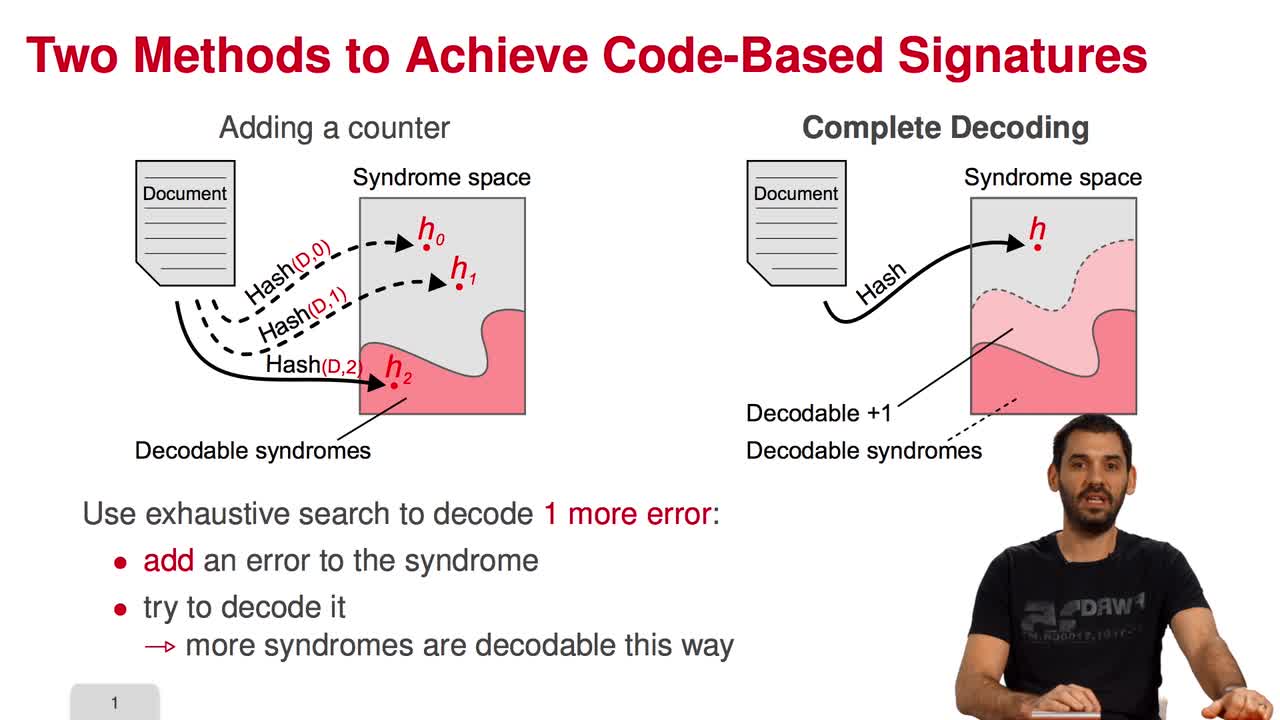
5.2. The Courtois-Finiasz-Sendrier (CFS) Construction
In this session, I am going to present the Courtois-Finiasz-Sendrier Construction of a code-based digital signature. In the previous session, we have seen that it is impossible to hash a document
5.3. Attacks against the CFS Scheme
In this session, we will have a look at the attacks against the CFS signature scheme. As for public-key encryption, there are two kinds of attacks against signature schemes. First kind of attack is
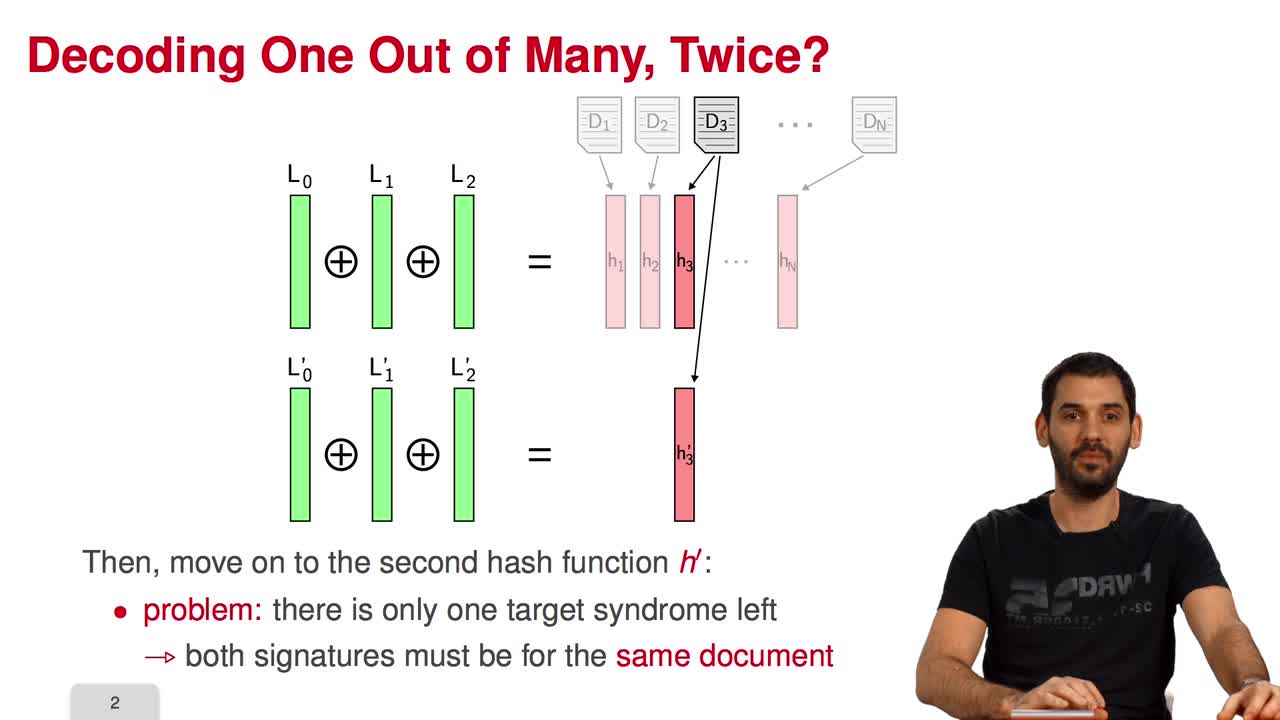
5.4. Parallel-CFS
In this session, I will present a variant of the CFS signature scheme called parallel-CFS. We start from a simple question: what happens if you try to use two different hash functions and compute
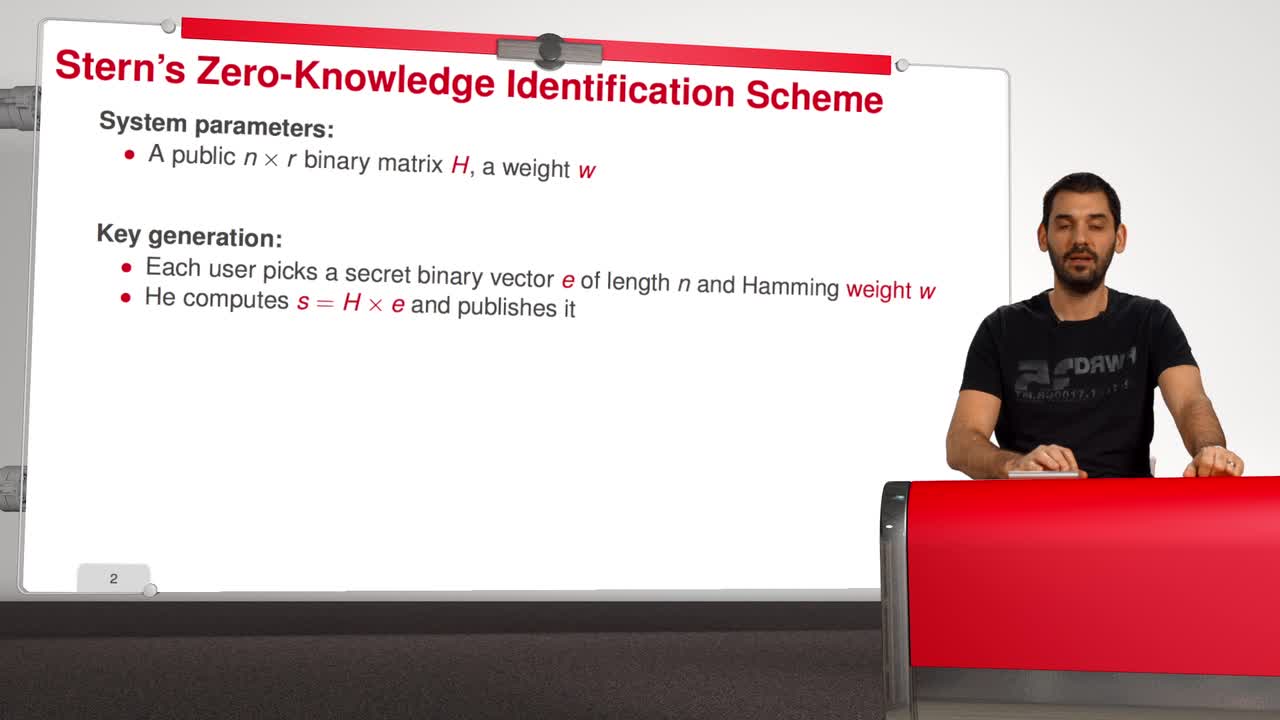
5.5. Stern’s Zero-Knowledge Identification Scheme
In this session, we are going to have a look at Stern’s Zero-Knowledge Identification Scheme. So, what is a Zero-Knowledge Identification Scheme? An identification scheme allows a prover to prove
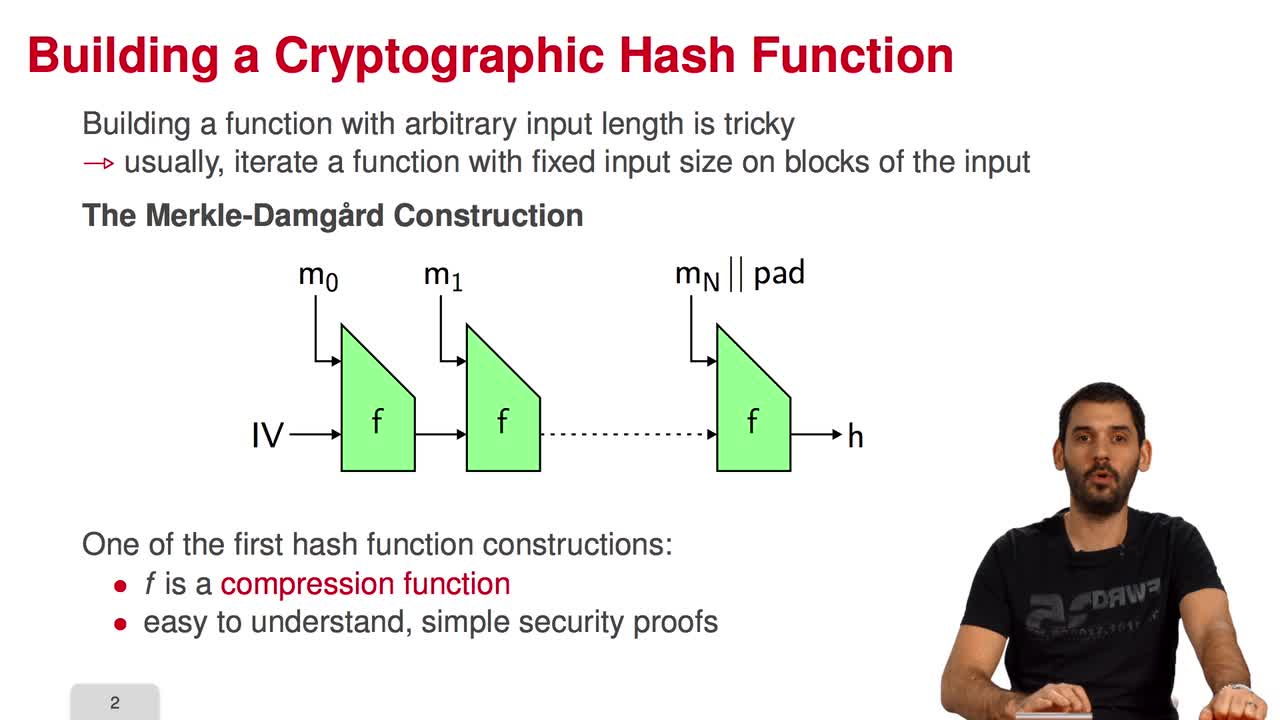
5.6. An Efficient Provably Secure One-Way Function
In this session, we are going to see how to build an efficient provably secure one-way function from coding theory. As you know, a one-way function is a function which is simple to evaluate and
5.7. The Fast Syndrome-Based (FSB) Hash Function
In the last session of this week, we will have a look at the FSB Hash Function which is built using the one-way function we saw in the previous session. What are the requirements for a
Intervenants et intervenantes
Auteur d'une thèse en mathématiques et informatique à l'Ecole polytechnique de Paris
Chercheuse à la faculté des sciences de l'université de La Laguna. Spécialités : code, cryptograhie et algèbre informatique (2015)
Enseignant chercheur en informatique à l'INRIA. Thèmes de recherche : Codes correcteurs d'erreurs et Cryptographie.