Notice
2.5. Critical Attacks - Semantic Secure Conversions
- document 1 document 2 document 3
- niveau 1 niveau 2 niveau 3
Descriptif
In this session, we willstudy critical attacks against the public-key cryptosystem.The partial knowledge on the plaintext reducesdrastically the computational cost of the attack to theMcEliece cryptosystem. For example, suppose that theadversary knows r bits of the plaintext. Then the difficulty ofrecovering the remaining k - r
bits in the completeMcEliece with parameters [n, k] isequivalent to that ofrecovering the full plaintext in
the McEliece withparameters [n, k - r]. This is given by this formula.You just need to observethis equation where G_I denotes the restriction of the matrix Gto the rows indexed by I. We study another attack, whichis called the reaction attack. In this attack, theadversary just needs to observe thereaction of thereceiver. So, this attack can be classified as a CCA butwith a weaker assumption.This attack rests uponthe following premise:a decoder will not attemptto correct a vector with t + 1 or more errors. The idea ofthe attack is the following:first of all, an adversaryflips one bit of the ciphertext. Then, the adversarytransmits the flipped ciphertext to the receiver andobserves his reaction. The receiver could havetwo possible reactions.
First reaction: if the flipped bit is an error-free position, thenthe ciphertext will have t + 1errors, so it isuncorrectable. The second reaction: ifi is an error position, thenthe flipped ciphertext willhave t - 1 error, and thereceiver will be able to decrypt it. We repeat this process forevery position until we have retrieved the error pattern. Another possible attack isthe resend-message attack. Note that the encryptionof the same message twice produces two differentciphertext. A message-resend condition can be easilydetected by observing the weight of the sum of the two ciphertexts.
Note that the sum of thetwo ciphertexts is the sum of the two errorvectors, what we have here. But, if the underlyingplaintexts are different, then the expected weight of the sum isabout the dimension of the code. Let
Intervention / Responsable scientifique
Dans la même collection
-
2.7. Reducing the Key Size - LDPC codes
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuLDPC codes have an interesting feature: they are free of algebraic structure. We will study in detail this proposal for the McEliece cryptosystem in this session. LDPC codes were originally
-
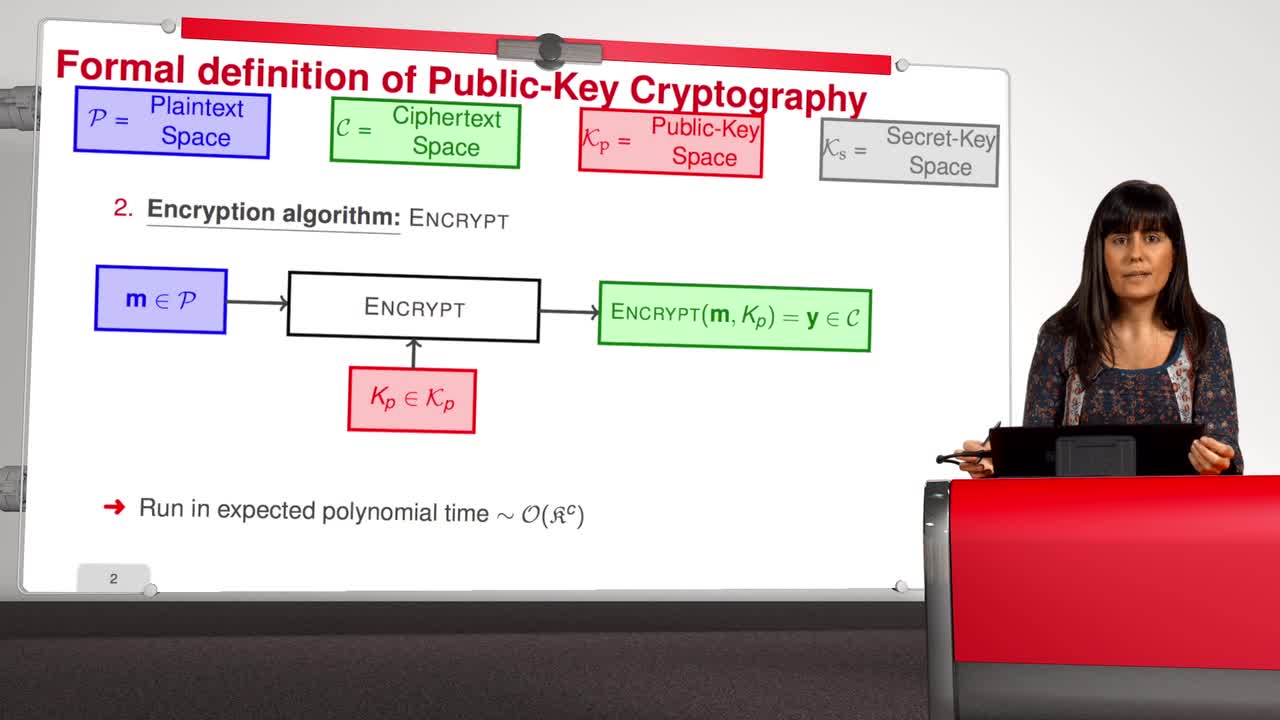
2.1. Formal Definition
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuWelcome to the second week of this MOOC entitled Code-Based Cryptography. This week, we will talk in detail about the McEliece cryptosystem. First, in this session, we will describe formally the
-
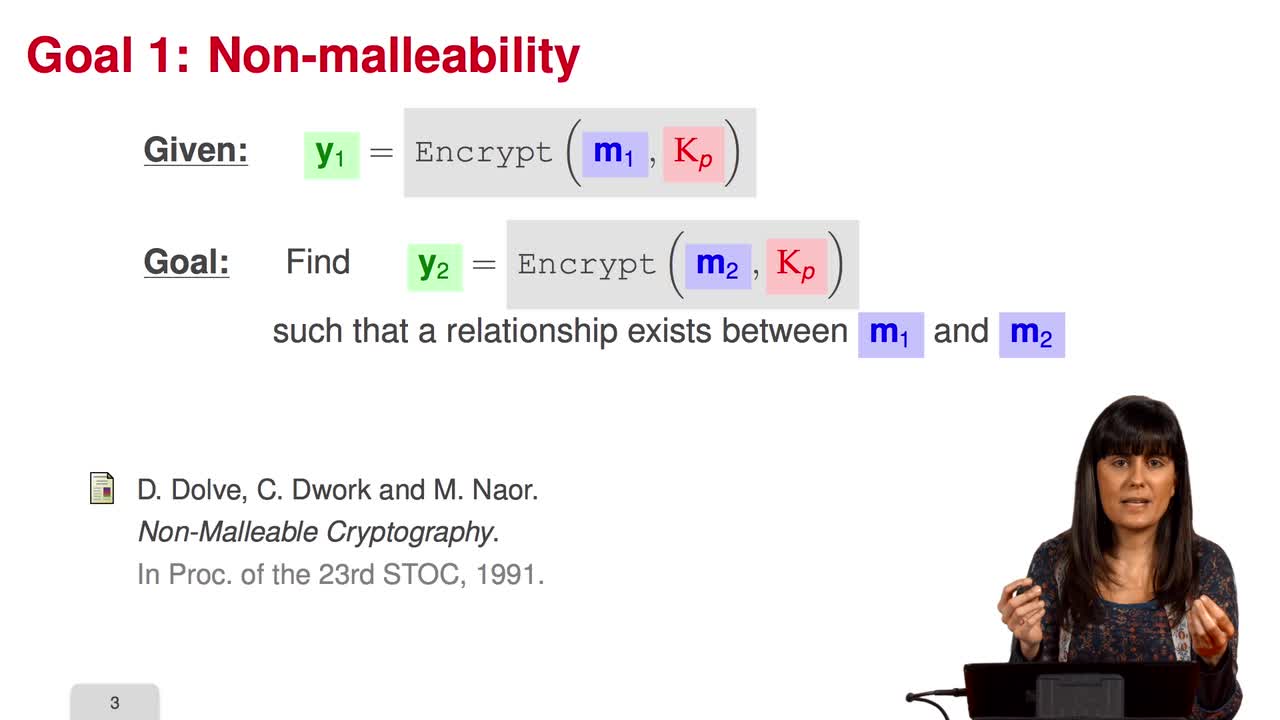
2.4. Notions of Security
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we will study the notion of security of public-key scheme. A public-key scheme is one-way if the probability of success of any adversary running in polynomial time is negligible.
-
2.8. Reducing the Key Size - MDPC codes
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuThis is the last session where we will talk about reducing the key size. Here we will introduce the MDPC codes. In 2012, the MDPC codes were proposed for the McEliece schemes. An MDPC code is a
-
2.2. Security-Reduction Proof
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuWelcome to the second session. We will talk about the security-reduction proof. The security of a given cryptographic algorithm is reduced to the security of a known hard problem. To prove that a
-
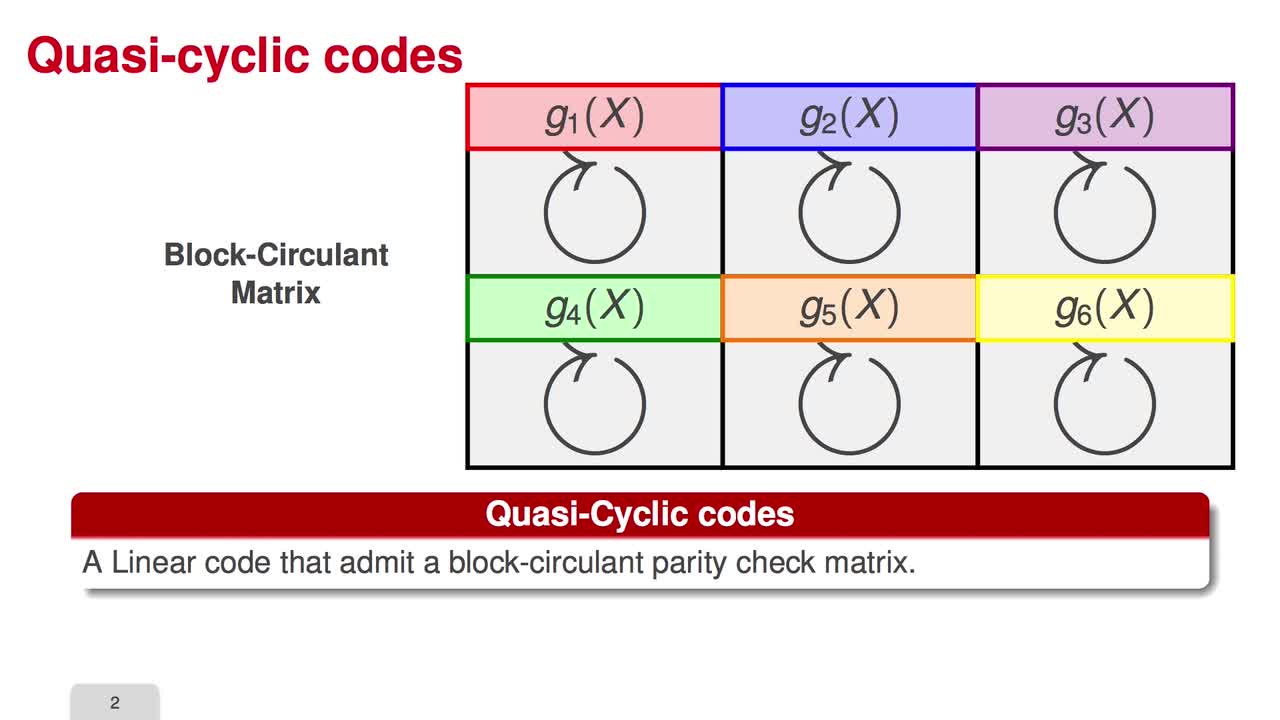
2.6. Reducing the Key Size
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn the next three sessions, I will explain how to reduce the key size of code-based cryptosystem. Circulant matrices are the central point in many attempts to reduce the key size of code-based
-
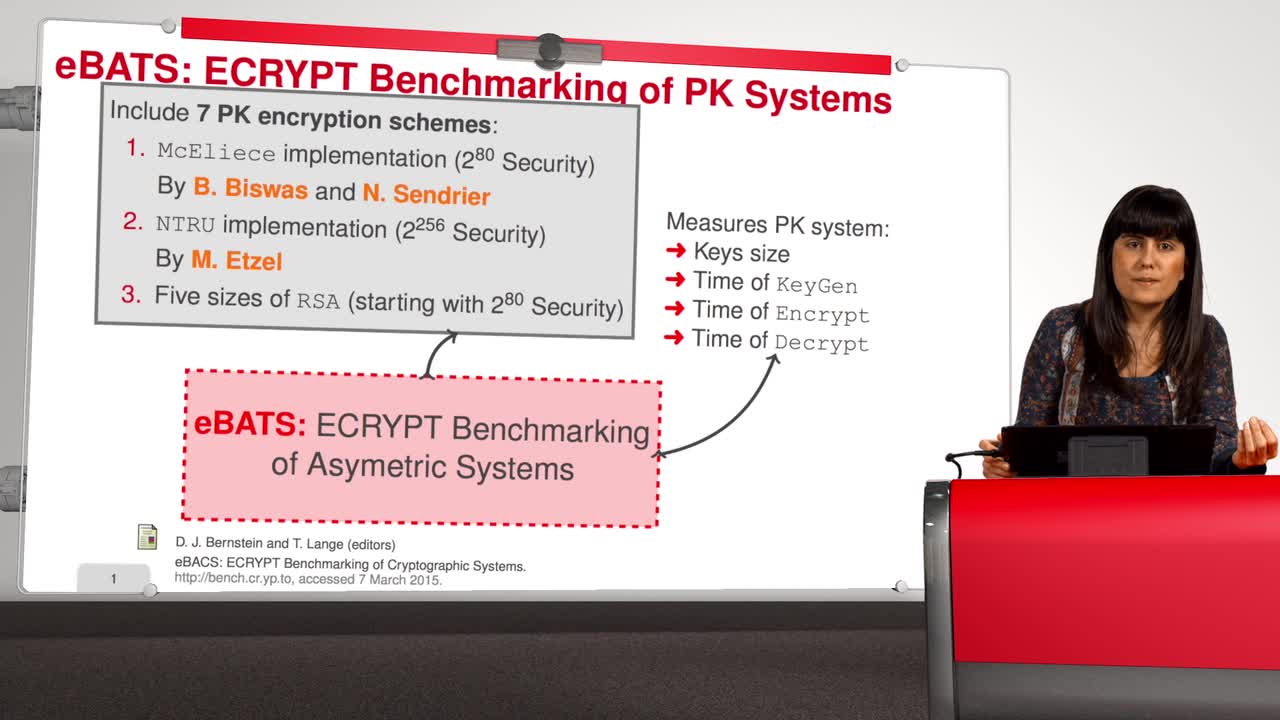
2.9. Implementation
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuThis is the last session of the second week. The cryptography community has different options for using public key cryptosystems, among others, they have RSA or DSA. But … McEliece has the same
-
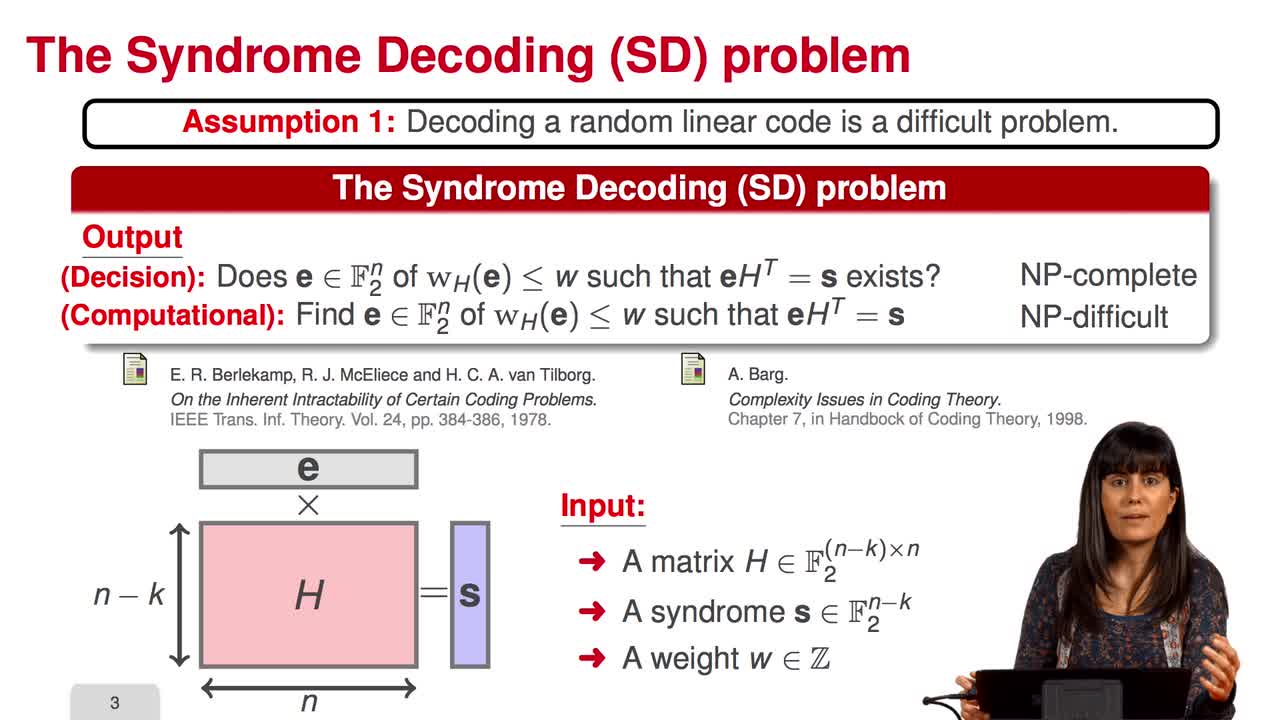
2.3. McEliece Assumptions
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we will talk about McEliece assumptions. The security of the McEliece scheme is based on two assumptions as we have already seen: the hardness of decoding a random linear code and
Avec les mêmes intervenants et intervenantes
-
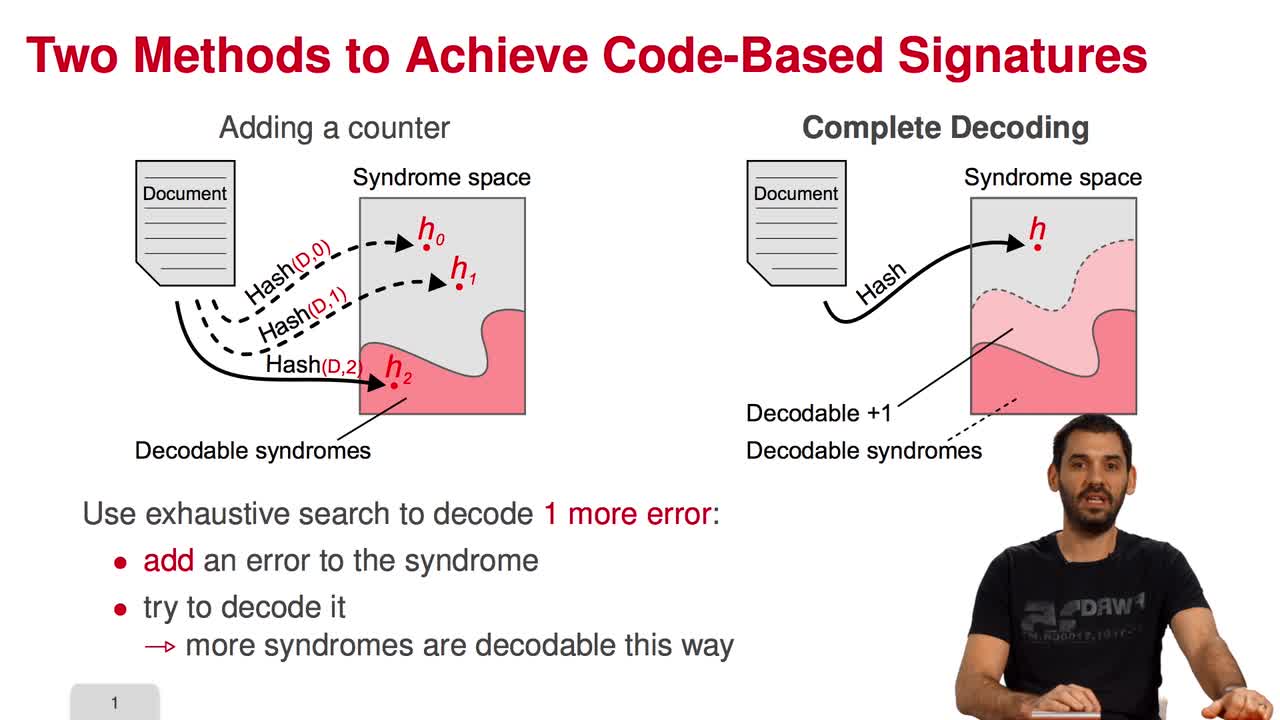
5.2. The Courtois-Finiasz-Sendrier (CFS) Construction
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, I am going to present the Courtois-Finiasz-Sendrier Construction of a code-based digital signature. In the previous session, we have seen that it is impossible to hash a document
-
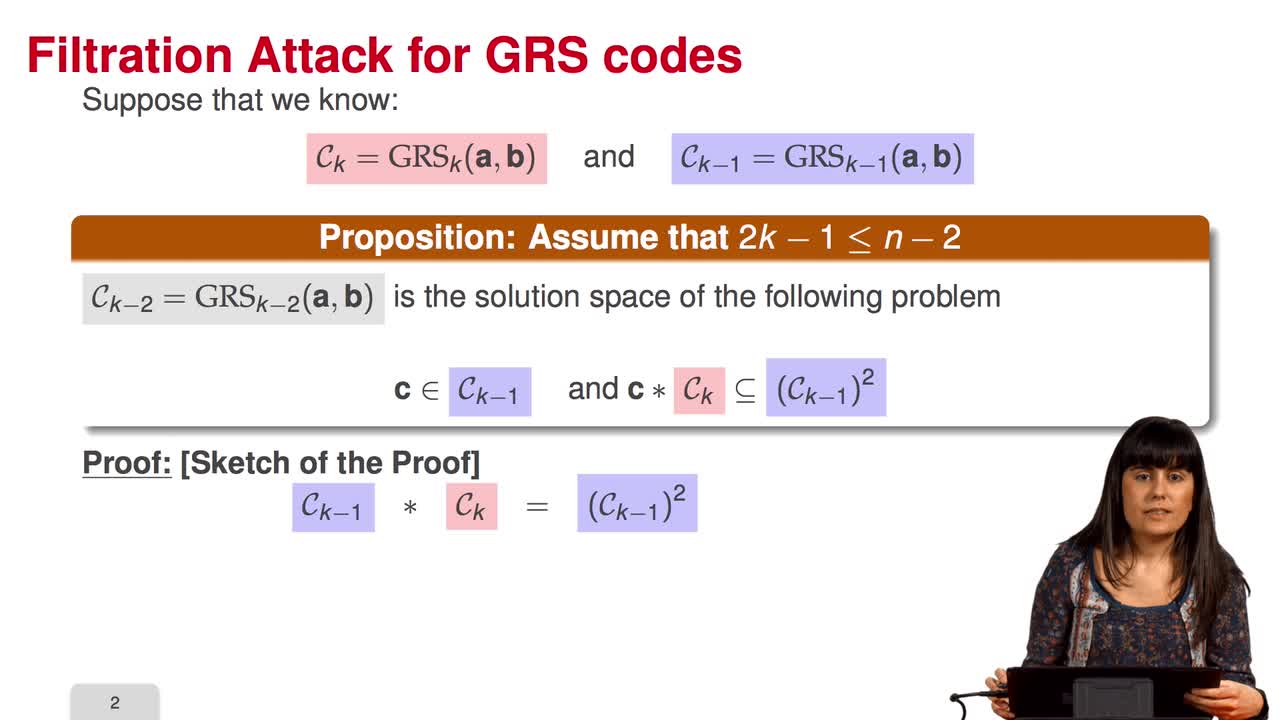
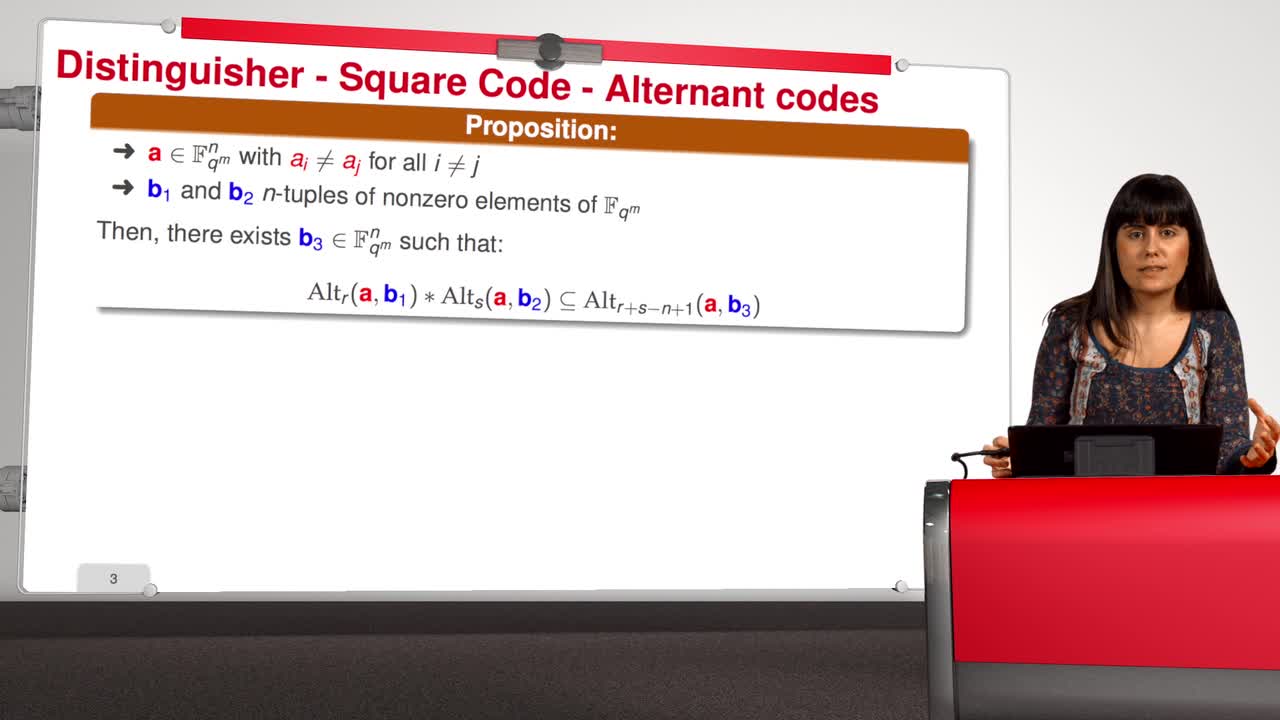
4.6. Attack against GRS codes
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session we will discuss the proposal of using generalized Reed-Solomon codes for the McEliece cryptosystem. As we have already said, generalized Reed-Solomon codes were proposed in 1986 by
-
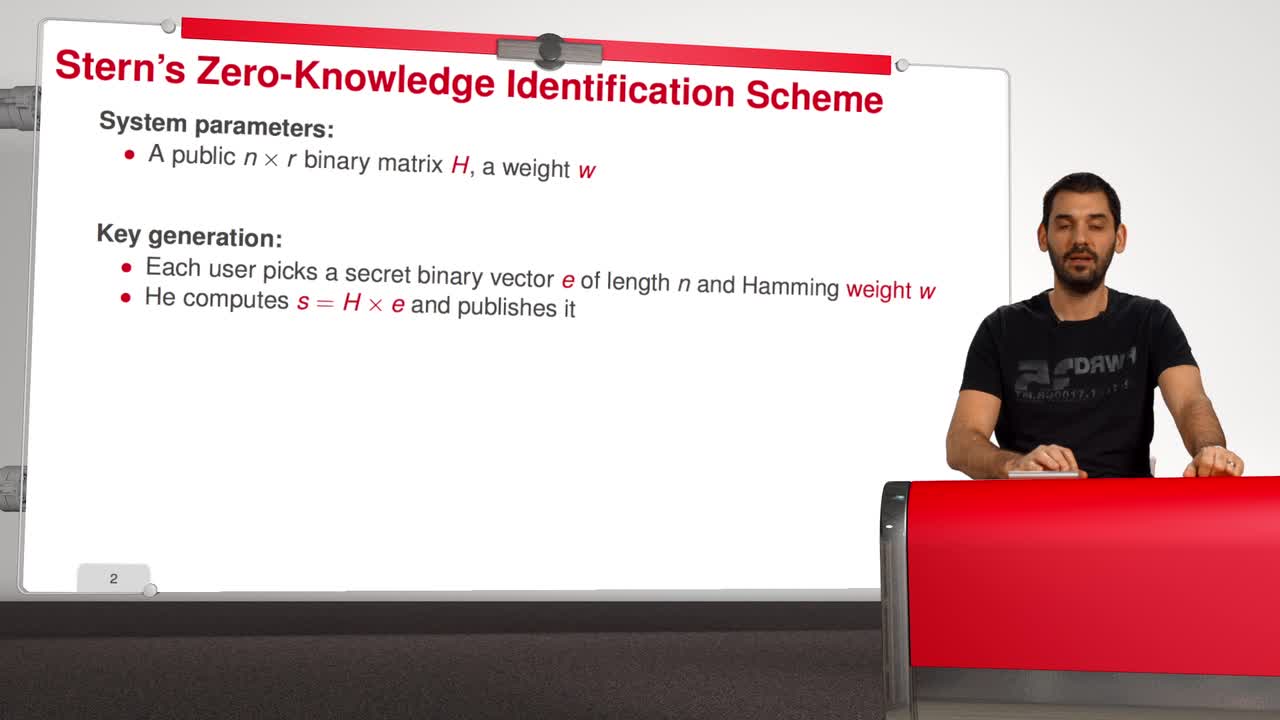
5.5. Stern’s Zero-Knowledge Identification Scheme
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we are going to have a look at Stern’s Zero-Knowledge Identification Scheme. So, what is a Zero-Knowledge Identification Scheme? An identification scheme allows a prover to prove
-
4.9. Goppa codes still resist
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuAll the results that we have seen this week doesn't mean that code based cryptography is broken. So in this session we will see that Goppa code still resists to all these attacks. So recall that
-
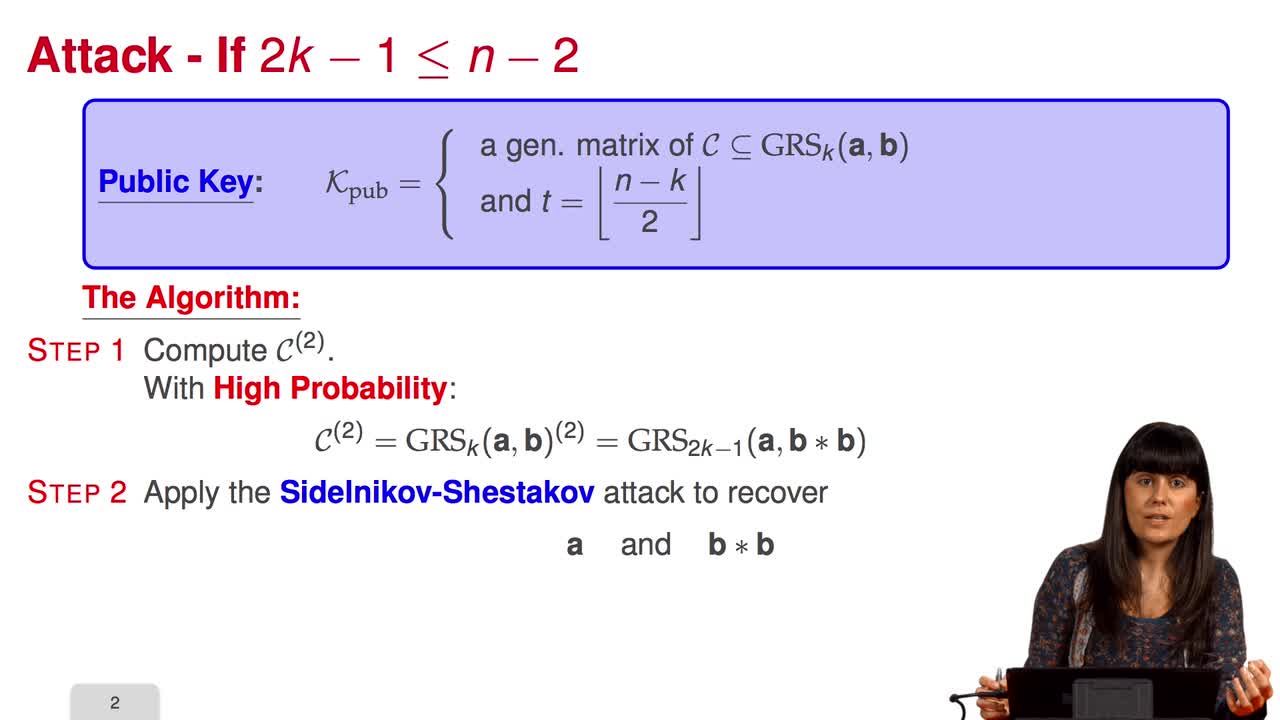
4.4. Attack against subcodes of GRS codes
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we will talk about using subcodes of a Generalized Reed–Solomon code for the McEliece Cryptosystem. Recall that to avoid the attack of Sidelnikov and Shestakov, Berger and
-
5.3. Attacks against the CFS Scheme
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we will have a look at the attacks against the CFS signature scheme. As for public-key encryption, there are two kinds of attacks against signature schemes. First kind of attack is
-
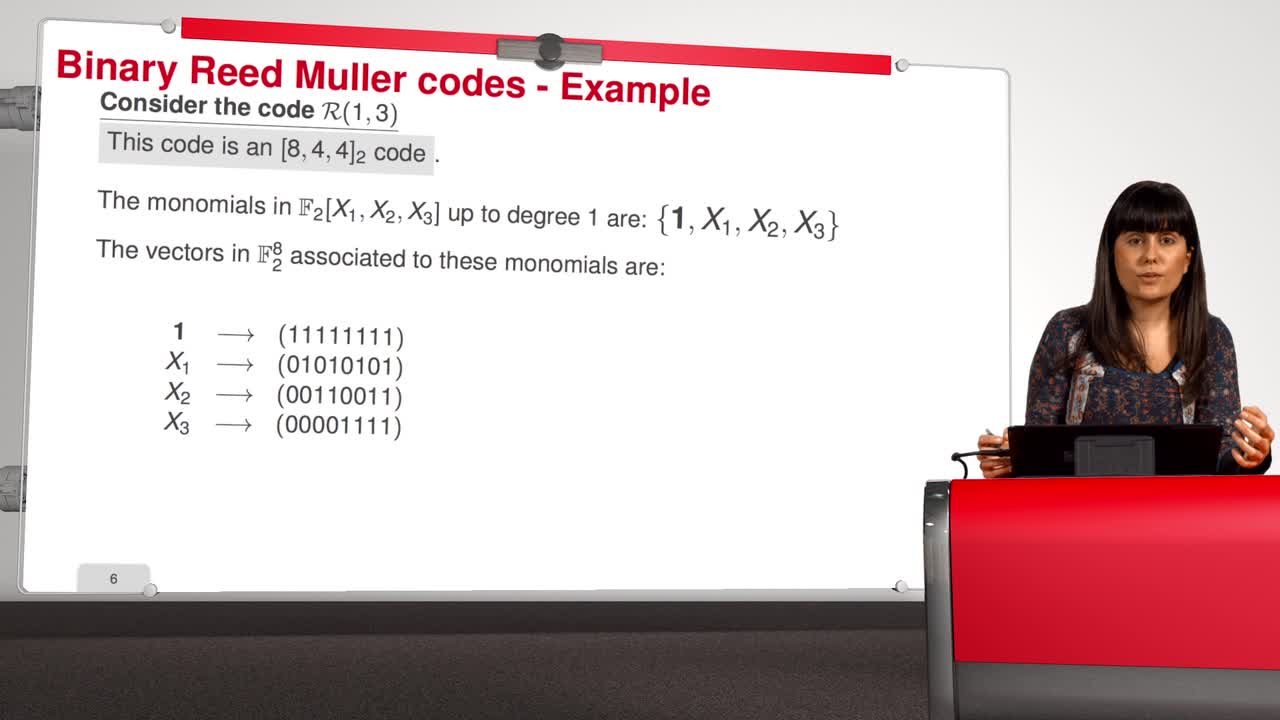
4.7. Attack against Reed-Muller codes
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we will introduce an attack against binary Reed-Muller codes. Reed-Muller codes were introduced by Muller in 1954 and, later, Reed provided the first efficient decoding algorithm
-
5.6. An Efficient Provably Secure One-Way Function
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we are going to see how to build an efficient provably secure one-way function from coding theory. As you know, a one-way function is a function which is simple to evaluate and
-
5.1. Code-Based Digital Signatures
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuWelcome to the last week of this MOOC on code-based cryptography. This week, we will be discussing other cryptographic constructions relying on coding theory. We have seen how to do public key
-
4.5. Error-Correcting Pairs
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuWe present in this session a general decoding method for linear codes. And we will see it in an example. Let C be a generalized Reed-Solomon code of dimension k associated to the pair (c, d). Then,
-
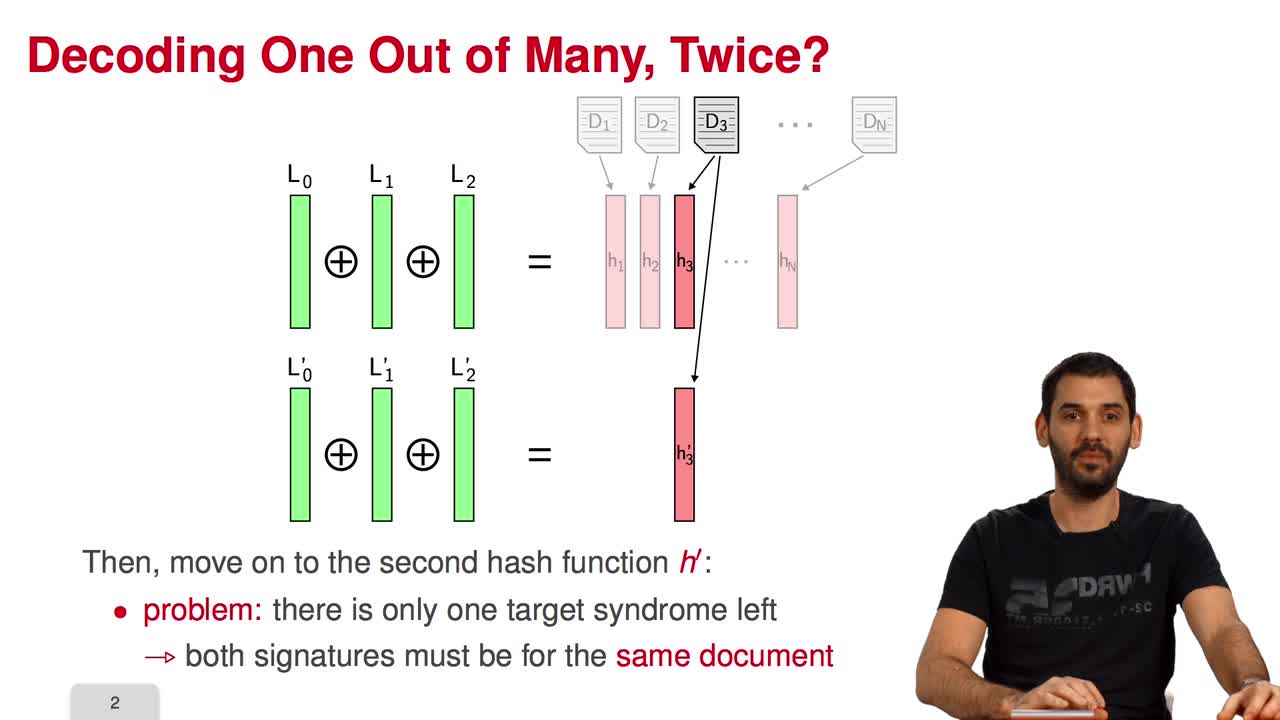
5.4. Parallel-CFS
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, I will present a variant of the CFS signature scheme called parallel-CFS. We start from a simple question: what happens if you try to use two different hash functions and compute
-
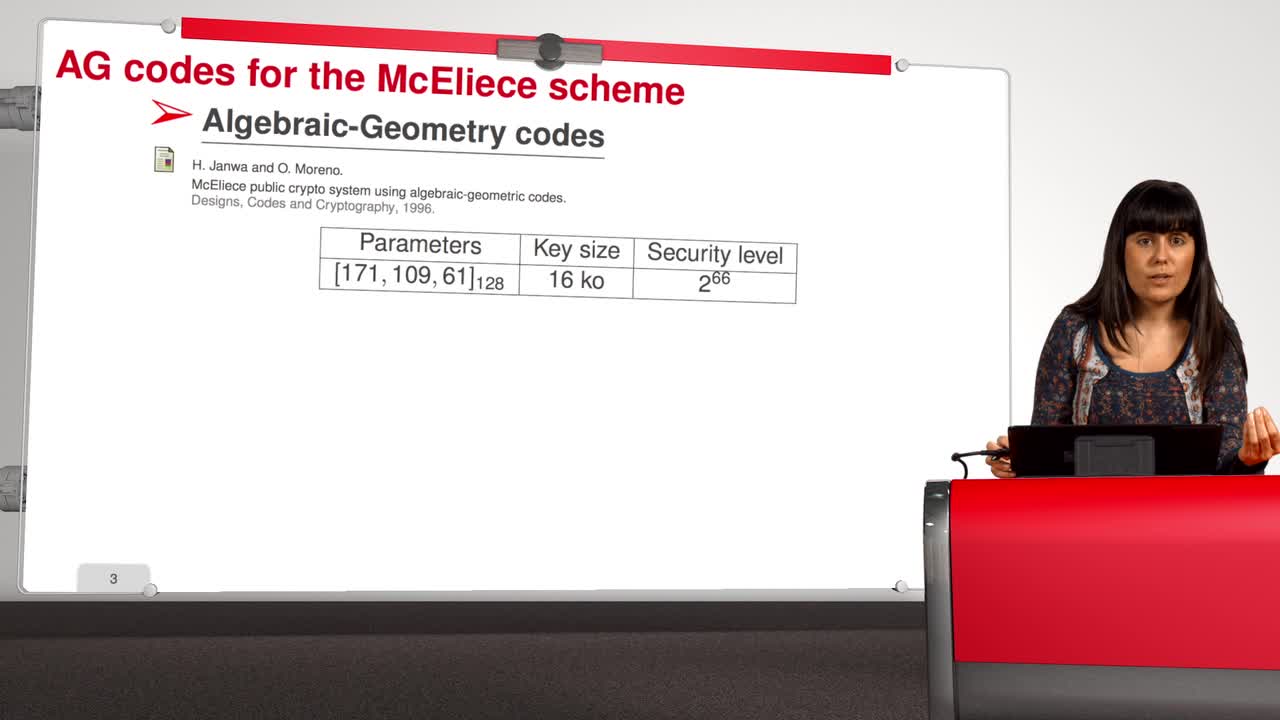
4.8. Attack against Algebraic Geometry codes
Marquez-CorbellaIreneSendrierNicolasFiniaszMatthieuIn this session, we will present an attack against Algebraic Geometry codes (AG codes). Algebraic Geometry codes is determined by a triple. First of all, an algebraic curve of genus g, then a n
Sur le même thème
-
Tuan Ta Pesao : écritures de sable et de ficelle à l'Ile d'Ambrym
VandendriesscheEricCe film se déroule au Nord de l’île d’Ambrym, dans l’archipel de Vanuatu, en Mélanésie...
-
Quel est le prix à payer pour la sécurité de nos données ?
MinaudBriceÀ l'ère du tout connecté, la question de la sécurité de nos données personnelles est devenue primordiale. Comment faire pour garder le contrôle de nos données ? Comment déjouer les pièges de plus en
-
Des systèmes de numération pour le calcul modulaire
BajardJean-ClaudeLe calcul modulaire est utilisé dans de nombreuses applications des mathématiques...
-
Inauguration de l'exposition - Vanessa Vitse : Nombres de Sophie Germain et codes secrets
VitseVanessaExposé de Vanessa Vitse (Institut Fourier) : Nombres de Sophie Germain et codes secrets
-
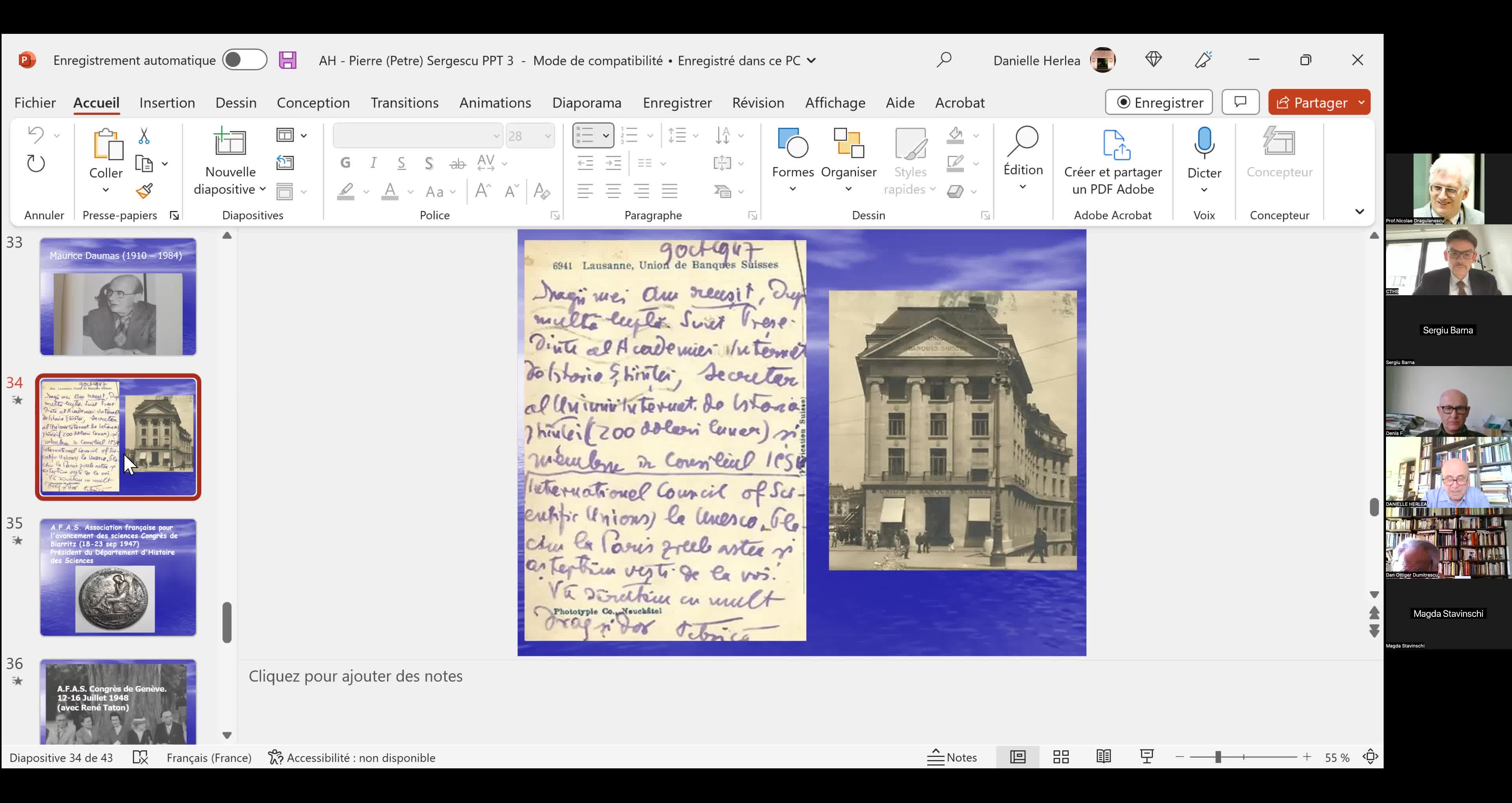
"Le mathématicien Petre (Pierre) Sergescu, historien des sciences, personnalité du XXe siècle"
HerléaAlexandreAlexandre HERLEA est membre de la section « Sciences, histoire des sciences et des techniques et archéologie industrielle » du CTHS. Professeur émérite des universités, membre effectif de l'Académie
-
Retour d'expérience sur l'utilisation croisée de plusieurs archives de fouilles
TufféryChristopheDans le cadre d'une thèse de doctorat engagée depuis 2019, une étude historiographique et épistémologique des effets des dispositifs numériques sur l'archéologie et sur les archéologues au cours des
-
Information Structures for Privacy and Fairness
PalamidessiCatusciaInformation Structures for Privacy and Fairness
-
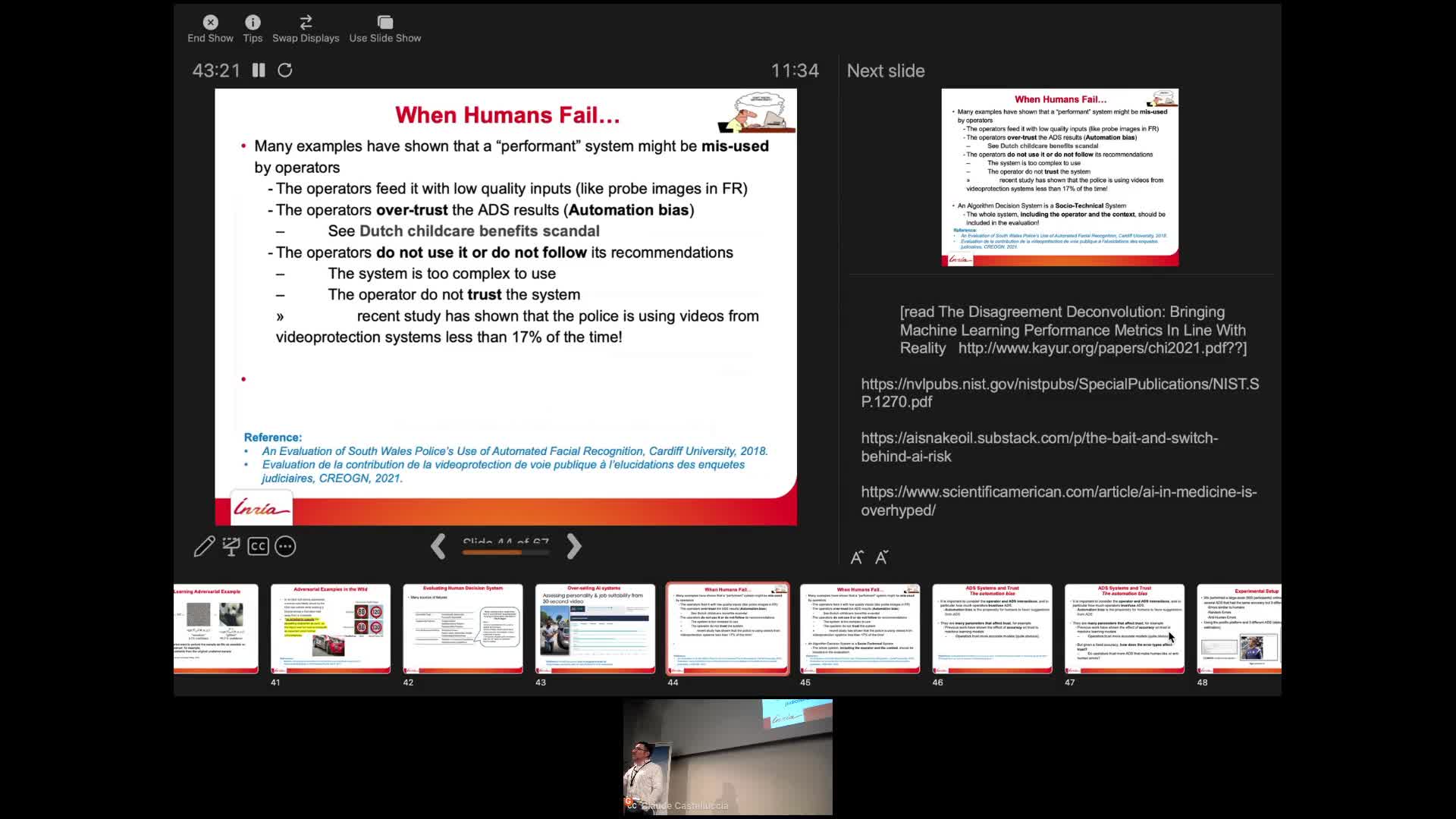
AI and Human Decision-Making: An Interdisciplinary Perspective
CastellucciaClaudeThis seminar will talk about some of the privacy risks of these systems and will describe some recent attacks. It will also discuss why they sometimes fail to deliver. Finally, we will also show that
-
Webinaire sur la rédaction des PGD
LouvetViolaineRédaction des Plans de Gestion de Données (PGD) sous l’angle des besoins de la communauté mathématique.
-
Alexandre Booms : « Usage de matériel pédagogique adapté en géométrie : une transposition à interro…
« Usage de matériel pédagogique adapté en géométrie : une transposition à interroger ». Alexandre Booms, doctorant (Université de Reims Champagne-Ardenne - Cérep UR 4692)
-
Présentation de la rencontre. A l’heure du numérique « Quelles mesures pour la mesure ? ». Le relev…
BadieAlainTardyDominiqueMalmaryJean-JacquesZugmeyerStéphanieRencontre-Atelier de l'ANR Ornementation Architecturale des Gaules. À l’heure du numérique, « Quelles mesures pour la mesure ? ». Le relevé des blocs d’architecture décorés et l’apport des outils
-
Photogrammétrie : Performances et limitations
EgelsYvesRencontre-Atelier de l'ANR Ornementation Architecturale des Gaules. À l’heure du numérique, « Quelles mesures pour la mesure ? ». Le relevé des blocs d’architecture décorés et l’apport des outils